InQuest helps organizations in both threat hunting and incident response through the use of RetroHunt®, our automated retrospective analysis capability. With our RetroHunt technology, your Security Operations Center (SOC) team can uncover historical threats, validate custom detection logic, and monitor for attacks or threat actors of interest.
RetroHunt aids our customers by providing them with a means of applying up-to-date knowledge to their historical data via YARA-compatible signatures to determine if any of the associated activity was present in the historical data. As new threat intel becomes available, RetroHunt automatically searches for IOCs across files that have already made it onto your system, minimizing threat dwell time.
One of the major features of the InQuest platform is providing the RetroHunt functionality and examination across the artifacts present in your environment. This analysis is performed automatically every week with each new signature pack release and/or update. It is also available as an on-demand feature that can be leveraged using both InQuest-issued and custom, user-defined signatures.
This feature enables users to search through many sessions and files with newly created or recently updated signatures. Weekly releases of new signatures ensure InQuest stays on top of the latest publicly disclosed exploits and emerging threats, while RetroHunt ensures you are alerted if that recently added threat coverage targeted your environment before public disclosure. Users can leverage the power of YARA by retroscanning with both InQuest proprietary signatures, as well as any User-Defined Signatures they’ve created within the platform.
Very often organizations do not know that a threat actor or malware has breached them until days, months, or even years after the initial intrusion. According to the Mandiant M-Trends report for 2023, the global median dwell time of an incident is down to 16 days from 21 since their previous report. This is due to the collective effort of defenders understanding these key vulnerabilities and TTPs, and sharing that information to drive down detection and response times. Rapid incident detection time is crucial in the remediation and mitigation of both known and unknown threats. It is also critical to have the ability to proactively monitor your environment for threat actor intrusion activity and malware of interest.
To help address these problems, InQuest provides customers with our unique RetroHunt feature across our three main products: FileTAC, NetTAC, and MailTAC. In combination with Deep File Inspection® (DFI), RetroHunt provides automated historical analysis across natively captured or ingested data as well as artifacts that are manually uploaded to the platform, including complete network sessions, files, and files derived through the DFI process. The default historical scanned data window is 14 days and can be customized by InQuest users. The available window is only limited by the size of your InQuest deployment’s datastore.
Keeping to the adage that “we are not as informed today as we are tomorrow,” a RetroHunt scan is performed automatically every time a new signature is added, whether from InQuest updates or User-Defined Signatures. This way, users are alerted to past threats as new intelligence surfaces continuously.
InQuest’s YARA integration also supports an extensive set of custom external variables that can be used by analysts and operators when writing rules to act against network traffic sessions, including those used with RetroHunt. We refer to signatures that aid this capability as Header Analytic signatures, and they support the most relevant network protocols and data types for modern threats, including:
- SMTP
- HTTP, including granular focus on the request URI
- TLS
- X.509 certificate data
- File artifact metadata
The Header Analytic capability allows InQuest customers to benefit from a level of abstraction, applying file inspection capabilities in YARA against network traffic inspection use cases in the most commonly used network protocols. Examples of how this may be applied include inspection of SMTP and HTTP protocol headers, matching of suspicious HTTP URI path and query parameters related to malware C2, and identification of malware-related SSL/TLS sessions using attributes such as JA3 fingerprints or certificate DNs. Capabilities related to in-depth inspection of original file artifacts, file metadata, and their DFI post-processed derived files. This set of InQuest-specific operators even covers inbound and outbound IP addresses as well as the associated ports for more stringent hunting, in scenarios when you know where on your network or how (tactically) to expect a particular attack.
Use Case: Threat Hunting
As security teams become more mature in their processes and methods, there comes a time when teams require the ability to proactively hunt and track specific threats targeting their environment. This is particularly the case as organizations seek to leverage threat intelligence to shift left in their security posture, helping minimize attacker dwell time in their network.
Analysts may be interested in a specific campaign or threat actor group that they have seen targeting other organizations in their sector or geographic region. Whether the original artifacts are collected from public or private sharing groups, in-house analysis, or open source intelligence (OSINT), this can all add up to generate a broader profile about the threat of interest.
After the identification and creation of an initial analysis profile, many artifacts make an excellent candidate for a set of User-Defined Signatures within the InQuest product line. These are then used to begin hunting with and allow well-placed collectors to catch all downstream session data–should that threat ever appear in your environment.
If these signatures match on encountered files or network sessions and generate alerts, users have the confidence to know they are protected, and they can immediately perform a RetroHunt. This look back in time allows the analysts to see if the threat has targeted them in the past. They can also view the full stream information on how that attack occurred. This forms the basis of a feedback cycle, providing analysts with further details on the threat, such as IP addresses used, file names, and other associated artifacts that can then be added back into the threat-hunting profile on an ongoing basis.
After expanding the threat profile from the InQuest discovered artifacts, analysts can then leverage our other integrations to collect indicators from additional available sources and begin to correlate these data points. These integrations include event data repositories such as Splunk and ArcSight, and malware analysis and triage options such as OPSWAT, Joe Sandbox and others. These tasks further build out the original threat profile – with all of this stemming from an analyst adding a signature and running a RetroHunt.
Use Case: Incident Response
Taking the recent case of a WinRAR 0-day vulnerability (CVE-2023-38831) as an example of the usefulness of RetroHunt, let’s follow the timeline of events from initial disclosure, in-the-wild usage, mainstream knowledge of the vulnerability, and public attack tool releases. With this exploit affecting WinRAR 6.22 and all earlier versions, this is of particular interest due to the extensive attack range; as well as the observed use by state-sponsored threat actors.
CVE-2023-38831 Timeline
Reference links for each table item are available in the appendix of this blog.
Though Group-IB covered and disclosed details on this exploit with mitigations released before publication, InQuest can assess with high confidence that both cybercriminals and advanced actors pay close attention to the same security advisory pages, blogs, and news feeds that defenders do. This was evident towards the end of 2023 when it was discovered by IBM’s X-Force that an APT was using this same exploit in an execution chain to target the critical energy infrastructure in Ukraine along with targeted attacks on other nations. Given the ease of deployment for this exploit and the widespread use of WinRAR, it’s likely that several users were targeted between April and October when the exploit was observed to be active in full swing.
Shortly after public disclosure, several GitHub repositories emerged containing all of the necessary instructions for reproducing this exploit. With this information documented and accessible, lesser-skilled cybercriminals and threat actors can easily prey on users with unpatched software.
These facts and timelines leave many unknowns when defending an environment:
- How long was this exploit being actively used before being discovered?
- Who is using the attack?
- What is the threat actor seeking in a targeted environment?
- Will widespread adoption appear soon?
- Most importantly, was your environment affected by this exploit before any public reporting was available?
This type of scenario is the perfect time to leverage RetroHunt.
Performing a RetroHunt
On the right-hand side of this image, the “Rescan Historical Content” menu is visible within the “RetroHunt” drop-down menu which allows users to search within given time-frames for this specific rule.
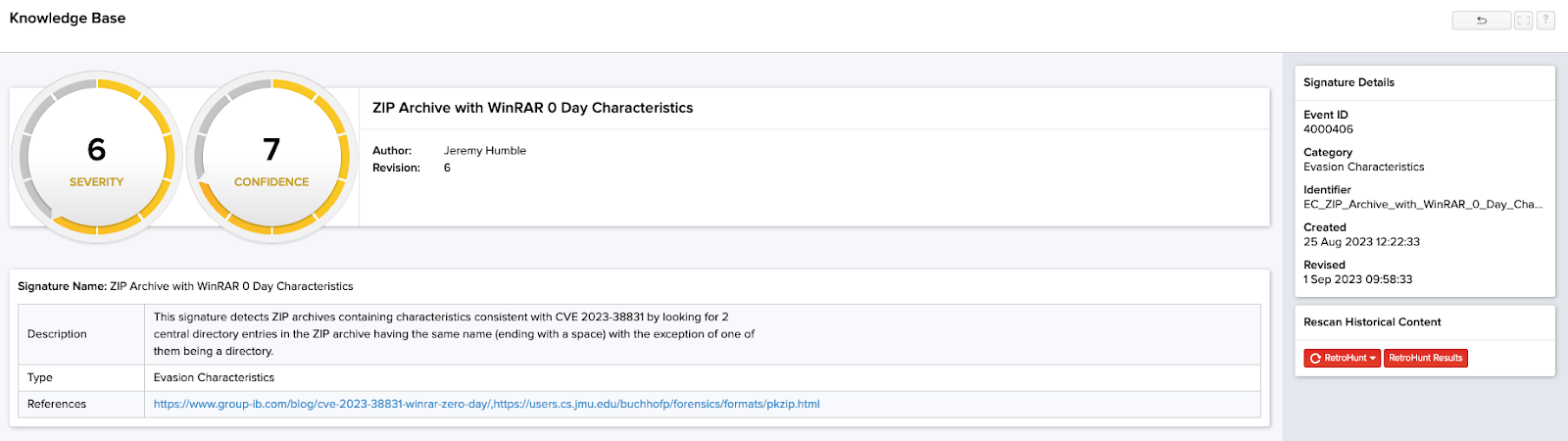
The RetroHunt retention period is only limited by the hardware your InQuest environment runs on, which allows you to check for the existence of this exploit, or any other new or updated threat, as far back as you would like. In the demo environment pictured, we can search backward 30 days from when the rule was published to detect any historical events leveraging this exploit and then immediately begin triaging the attack.
If discovered, analysts can view the malicious file’s metadata, including other signatures the artifact may have also triggered on, and they can pivot into every unique session where the exploit content or associated file or session data was found.
Conclusion
A SOC or Threat Intelligence team is only as good as the data it receives and how fast it can be acted on. With the InQuest signatures, RetroHunt built into InQuest, and automatic execution of RetroHunts after every weekly release, customers can stay up-to-date on the latest threats and quickly become aware of past threats that bypass other common detection methods. This ability allows users to quickly determine which assets have been affected and prioritize response to the identified threat much more efficiently. In the world of incident response, every second can make the difference between containment and infection.
References
Sources used above in the CVE-2023-38831 timeline:
- https://www.bleepingcomputer.com/news/security/winrar-zero-day-exploited-since-april-to-hack-trading-accounts/
- https://www.win-rar.com/singlenewsview.html?&L=0&tx_ttnews%5Btt_news%5D=230&cHash=d5b004cf8e13ffaf713f4ec6b604694e
- https://www.group-ib.com/blog/cve-2023-38831-winrar-zero-day/
- https://github.com/BoredHackerBlog/winrar_CVE-2023-38831_lazy_poc
- https://www.cve.org/CVERecord?id=CVE-2023-38831
- https://securityintelligence.com/x-force/itg05-ops-leverage-israel-hamas-conflict-lures-to-deliver-headlace-malware/
How Effective Is Your Email Security Stack?
Did you know, 80% of malware is delivered via email? How well do your defenses stand up to today’s emerging malware? Discover how effectively your email provider’s security performs with our Email Attack Simulation. You’ll receive daily reports on threats that bypassed your defenses as well as recommendations for closing the gap. Free of charge for 30 days.
